
Think your WordPress site is secure? You might be shocked to learn that 97% of WordPress security problems stem from plugin vulnerabilities alone. Even worse, hackers know exactly which mistakes you're making, and they're counting on you to keep making them.
Don't panic. Most WordPress security breaches happen because site owners unknowingly leave the digital equivalent of their front door wide open. The good news? These mistakes are completely preventable once you know what to look for.
Let's dive into the seven most dangerous security mistakes that make your WordPress site an easy target for cybercriminals.
1. Running Outdated or Inactive Plugins
Here's a scary statistic: only 30% of WordPress users have auto-updates enabled on their websites. That means 70% are sitting ducks for hackers who specifically target outdated plugins.

How Hackers Exploit This: Cybercriminals use automated scanning tools that crawl the web looking for sites running vulnerable plugin versions. When they find one, they already have the exploit code ready to go. It's like leaving your house key under the doormat with a sign pointing to it.
Take the 2023 vulnerabilities in WP Fastest Cache and Essential Add-ons for Elementor. Thousands of websites running outdated versions became instant targets. Hackers didn't need to be clever, they just needed to find sites that hadn't updated.
The Fix: Enable automatic updates for plugins whenever possible. If you prefer manual control, check for updates weekly. More importantly, delete any plugins you're not actively using. Inactive plugins are still attack vectors that hackers love to exploit.
2. Using Weak Passwords and Skipping Two-Factor Authentication
Here's a reality check: 41% of WordPress users don't use strong passwords or two-factor authentication (2FA). If your admin password is "password123" or your business name plus the year, you're basically sending hackers an invitation.
How Hackers Exploit This: Brute force attacks are the digital equivalent of trying every key until one opens the lock. Hackers use bots that attempt thousands of login combinations per minute. Since WordPress allows unlimited login attempts by default, these bots can run 24/7 until they crack your password.
Once they're in, they own your site. Customer data, financial information, email addresses, everything becomes theirs to sell or exploit.
The Fix: Use passwords that are at least 12 characters long with a mix of letters, numbers, and symbols. Better yet, use a password manager to generate unique passwords for every account. Enable 2FA immediately, Google's research shows it stops 100% of automated bot attacks.
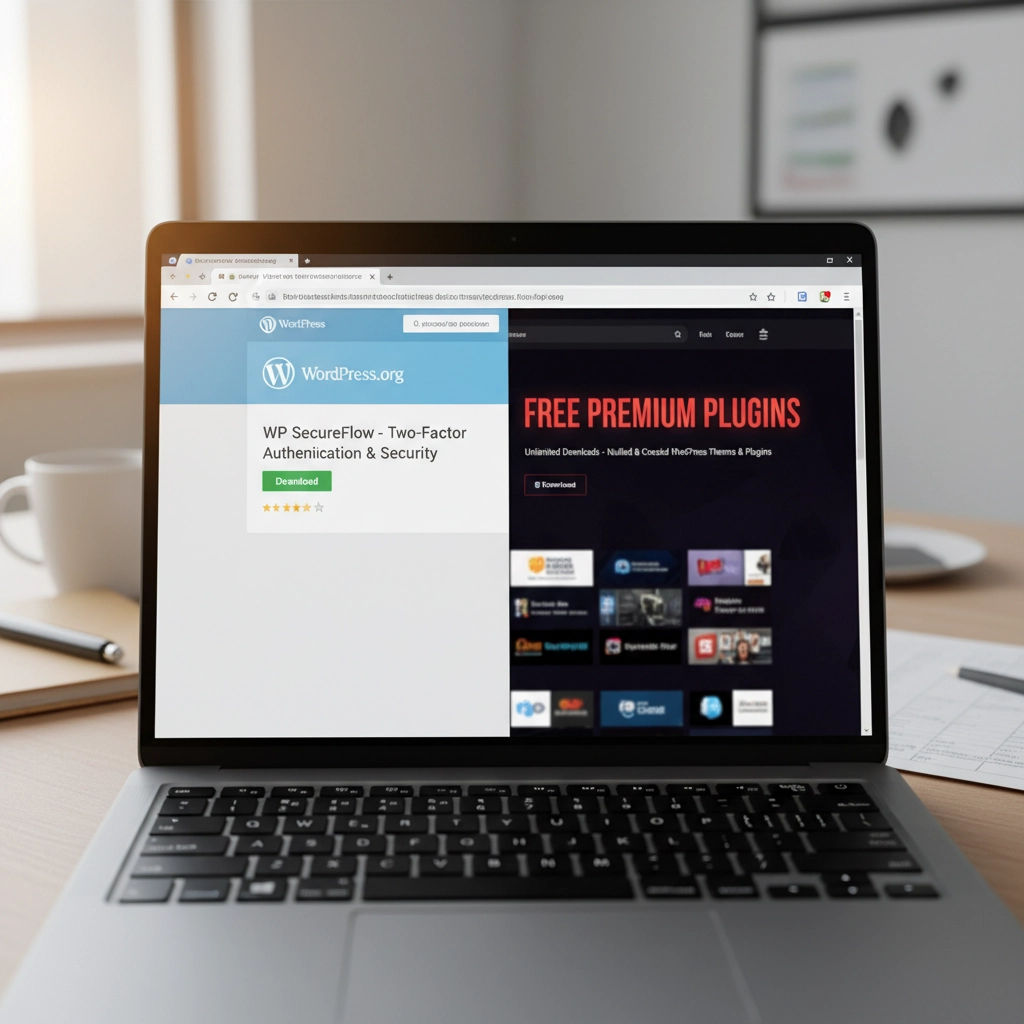
3. Installing Plugins and Themes from Sketchy Sources
Free premium themes and plugins sound tempting, right? Those "nulled" versions of expensive plugins seem like a steal. Here's the truth: if something seems too good to be true, it probably contains malware.
How Hackers Exploit This: Malicious developers embed backdoors directly into these "free" premium plugins. The moment you install them, hackers have a secret entrance to your site. Some plugin viruses are designed to automatically infect every other plugin and theme on your installation, spreading like wildfire through your entire WordPress setup.
These backdoors often go undetected for months, giving hackers plenty of time to steal data, inject spam links, or use your server for cryptocurrency mining.
The Fix: Stick to plugins and themes from WordPress.org, reputable commercial developers, or well-established marketplaces. Yes, you might pay more upfront, but it's infinitely cheaper than dealing with a hacked website.
4. Ignoring File Permissions
File permissions might sound technical, but they're basically your site's security guard. When configured incorrectly, they're like having a security guard who lets anyone walk into your building.
How Hackers Exploit This: Loose file permissions allow attackers to access sensitive files they shouldn't see. Once they have limited access, they can often escalate their privileges and gain control of critical system files. It's like giving someone permission to use your bathroom, and they end up with keys to your entire house.
With proper access, hackers can modify your site's code, steal database information, or install persistent backdoors that survive even when you clean up other security issues.
The Fix: Follow the principle of least privilege. Files should be set to 644 permissions, directories to 755. Your wp-config.php file should be 600. If these numbers look like gibberish, ask your hosting provider to audit your file permissions.
5. Procrastinating on WordPress Updates
Those update notifications aren't suggestions: they're security bulletins. Every WordPress update includes patches for newly discovered vulnerabilities. When you ignore them, you're essentially leaving known security holes open for hackers to exploit.
How Hackers Exploit This: WordPress developers openly publish what each security update fixes. This creates a roadmap for hackers who can easily identify which sites haven't updated and target the specific vulnerabilities that remain unpatched.
It's like fixing a broken lock on your front door but announcing to the neighborhood exactly when the repair will happen. Unpatched sites become obvious targets.
The Fix: Update WordPress core, plugins, and themes as soon as updates become available. Schedule a weekly maintenance window to check for and install updates. Most hosting providers offer staging environments where you can test updates before applying them to your live site.
6. Skipping Backups and Security Monitoring
Not having backups is like driving without insurance: you'll only realize how crucial it is when disaster strikes. Similarly, running a WordPress site without security monitoring is like closing your eyes and hoping nothing bad happens.
How Hackers Exploit This: Without backups, when (not if) your site gets compromised, you have no clean version to restore. Hackers know this, which is why some attacks are designed to corrupt or encrypt your existing files, leaving you with no recovery options.

Without security monitoring, attacks can run undetected for weeks or months. During this time, hackers can steal customer data, inject malicious code, or use your site to attack other websites.
The Fix: Set up automated daily backups stored off-site (not on the same server as your website). Install a security plugin that monitors file changes, login attempts, and suspicious activity. For critical business sites, consider our email security services that include comprehensive monitoring.
7. Installing Software from Unknown Repositories
This mistake often flies under the radar but can be the most dangerous. Installing plugins or themes from forums, random websites, or commercial repositories outside the WordPress ecosystem introduces unknown code into your installation.
How Hackers Exploit This: Unlike WordPress.org plugins that undergo community scrutiny, third-party sources may lack any security review process. These repositories are often intentionally compromised or simply don't have the resources to properly vet code.
Hackers exploit this by creating legitimate-looking plugins or themes that contain hidden malware. Once installed, these give attackers automatic access to your site without needing to break in through other methods.
The Fix: Stick to WordPress.org for free plugins and themes. For premium options, buy directly from the developer or established marketplaces like CodeCanyon. Never download "nulled" versions of paid plugins: they're almost always infected with malware.
Your Next Steps
WordPress security isn't rocket science, but it does require consistent attention. Start by auditing your current setup against these seven mistakes. Update everything, remove unused plugins, strengthen your passwords, and enable 2FA.
Remember, hackers are counting on you to make these mistakes. Don't give them the satisfaction. A few hours of security maintenance now can save you weeks of cleanup later: not to mention the potential loss of business and customer trust.
Need help securing your WordPress site? We specialize in helping businesses protect their digital assets without the technical headaches. Your website is too important to leave to chance.



 European Union General Data Protection Regulation Compliant
European Union General Data Protection Regulation Compliant