by Charles Oropallo | Oct 23, 2025 | Email, Security, Technical Help
 Phishing attacks have become more sophisticated than ever in 2025. Cybercriminals now use AI to craft convincing emails that mimic your trusted contacts perfectly. They’re targeting small businesses more aggressively because they know you might not have enterprise-level security budgets.
Phishing attacks have become more sophisticated than ever in 2025. Cybercriminals now use AI to craft convincing emails that mimic your trusted contacts perfectly. They’re targeting small businesses more aggressively because they know you might not have enterprise-level security budgets.
But here’s the good news: protecting your inbox doesn’t require expensive solutions or a computer science degree. You just need to know what to look for and implement a few key safeguards. Think about what’s connected to your email accounts – your banking, your customer data, your business operations. That’s why phishing avoidance should be your top priority this year.
Let’s dive into practical steps you can take today to bulletproof your inbox against these increasingly clever attacks.
Set Up Email Authentication to Block Impersonators
Email authentication is your first line of defense against domain spoofing. When someone tries to send emails pretending to be from your business, these protocols will catch them.
SPF (Sender Policy Framework) tells email servers which IP addresses are allowed to send emails from your domain. Think of it as a guest list for your domain – only approved senders get through.
DKIM (DomainKeys Identified Mail) adds a digital signature to your outgoing emails. It’s like a tamper-proof seal that proves the message really came from you and wasn’t altered in transit.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) combines SPF and DKIM, then tells other email servers what to do with emails that fail these checks. You can set it to quarantine suspicious emails or reject them entirely.
Setting up these protocols requires adding DNS records to your domain. If that sounds intimidating, most hosting providers or IT consultants can handle this quickly. The investment pays off immediately – you’ll see fewer spoofed emails reaching your contacts and customers.
Recognize the New Generation of Phishing Emails
Today’s phishing emails are getting scary good at mimicking legitimate communications. AI helps scammers create perfect grammar, use your company’s writing style, and even reference recent events or conversations.
Watch for these red flags that still give away phishing attempts:
Suspicious sender addresses often use lookalike domains. Instead of “fedex.com,” you might see “fedx-support.com” or “fedex-delivery.net.” Always check the actual sender address, not just the display name.
Urgent language designed to bypass your critical thinking. Phrases like “immediate action required,” “account will be closed,” or “verify within 24 hours” should trigger your skepticism.
Generic greetings like “Dear Customer” instead of your actual name. Legitimate businesses usually personalize their communications, especially for account-related messages.
Mismatched links where the displayed text says one thing but the actual URL leads somewhere else. Hover over links before clicking to see where they really go.
Unexpected attachments requiring immediate download or execution. Be especially wary of .zip files, .exe files, or documents with embedded macros from unknown senders.
Implement Smart Behavioral Practices
Your daily email habits matter more than any security software. Small changes in how you handle emails can prevent most successful phishing attacks.
Never click links in emails unless you absolutely trust the sender. When in doubt, open a new browser window and navigate to the company’s website directly. This simple practice stops most credential theft attempts cold.
Verify suspicious requests through alternative channels. If your “boss” emails asking for urgent wire transfers or sensitive information, pick up the phone and confirm. Scammers count on you following email instructions without verification.
Keep your software updated. Email clients, browsers, and operating systems regularly patch security vulnerabilities that phishers exploit. Enable automatic updates whenever possible.
Use different passwords for different accounts. When one account gets compromised, you don’t want attackers accessing everything else. Password managers make this easier by generating and storing unique passwords for each service.
Deploy Multi-Factor Authentication Strategically
Multi-factor authentication (MFA) blocks most phishing attacks even when criminals steal your password. But not all MFA is created equal in 2025.
Avoid SMS-based authentication when possible. Scammers can intercept text messages or use social engineering to redirect your phone number. It’s better than nothing, but other options provide stronger protection.
App-based authentication using Google Authenticator or Microsoft Authenticator offers better security. These generate time-based codes that work even without internet connectivity.
Hardware security keys like YubiKey provide the strongest protection against phishing. They use cryptographic proof that can’t be phished, even by sophisticated attacks. For businesses handling sensitive data, this investment pays for itself quickly.
Choose the Right Email Security Tools
Modern email security goes beyond basic spam filtering. AI-powered solutions can detect subtle patterns that humans might miss.
Advanced threat protection services analyze email content, sender behavior, and link destinations in real-time. They catch zero-day phishing attempts that haven’t been reported yet.
Email sandboxing opens suspicious attachments in isolated environments to check for malware before they reach your inbox. This protects against document-based attacks that bypass traditional antivirus.
User reporting tools make it easy for your team to flag suspicious emails. Many security platforms learn from these reports, improving protection for everyone.
Link rewriting services intercept clicks on suspicious URLs and scan them before allowing access. This provides a safety net when users click without thinking.
Train Your Team Without Boring Them
Security awareness training works best when it’s relevant and engaging. Skip the generic presentations and focus on real scenarios your business might face.
Run phishing simulations that mimic actual threats targeting your industry. Banking clients might see fake loan notifications, while retail businesses could see shipping updates. Make the training relevant to daily operations.
Create a no-blame reporting culture. Team members should feel comfortable reporting suspicious emails without fear of embarrassment. Praise people for being cautious – it’s exactly the behavior you want.
Share recent examples of phishing attempts targeting similar businesses. Real-world cases are more memorable than theoretical scenarios.
Keep sessions short and focused. Fifteen-minute monthly updates work better than annual marathon training sessions. People retain information better in small, digestible pieces.
Protect Your Business Email Specifically
Business email faces unique threats that personal email doesn’t encounter. Attackers research your company structure, recent news, and business relationships to craft targeted attacks.
Business Email Compromise (BEC) attacks target financial processes. Scammers impersonate executives or vendors to trick employees into wire transfers or credential sharing. Always verify payment requests through secondary channels.
Supply chain phishing uses compromised vendor accounts to attack customers. Even trusted partners can become unwitting attack vectors. Maintain healthy skepticism even with familiar senders.
CEO fraud targets employees with fake urgent requests from leadership. Attackers study your organizational chart and communication patterns to make requests seem legitimate.
Keep Your Defenses Current
Phishing tactics evolve constantly, so your protection strategies must evolve too. What worked last year might not catch this year’s threats.
Monitor your email authentication reports. DMARC generates reports showing who’s trying to send emails from your domain. Review these monthly to catch impersonation attempts early.
Update your security awareness training quarterly with new threat examples. Cybercriminals adapt their tactics based on what works, so your team needs to stay current.
Test your backup and recovery procedures. Even with perfect prevention, some attacks might succeed. Regular testing ensures you can recover quickly without paying ransoms or losing critical data.
Review and update your incident response plan. Everyone should know who to contact and what steps to take when phishing attacks succeed. Quick response can minimize damage significantly.
Take Action Today
Phishing avoidance isn’t something you can set up once and forget. It requires ongoing attention and regular updates. But the effort protects your business reputation, customer data, and financial security.
Start with email authentication – SPF, DKIM, and DMARC records provide immediate protection against domain spoofing. Then implement multi-factor authentication on critical accounts. These two steps alone will block most common phishing attacks.
Train your team to recognize and report suspicious emails. Create processes for verifying unexpected requests through alternative communication channels. The combination of technology and smart human behavior creates a robust defense against even sophisticated attacks.
Remember, cybercriminals are running businesses too. They target victims who look like easy marks and move on when defenses are strong. Make your business a hard target, and attackers will focus their efforts elsewhere.
For additional technical help with email security implementation, check out our email security resources for step-by-step guidance on protecting your business communications.










by Charles Oropallo | Sep 18, 2025 | Email, Security
 Think your business emails are secure? Think again. Every day, cybercriminals send millions of fake emails pretending to be from legitimate businesses. Without proper email authentication, your company name could be next.
Think your business emails are secure? Think again. Every day, cybercriminals send millions of fake emails pretending to be from legitimate businesses. Without proper email authentication, your company name could be next.
Here’s the scary truth: anyone can send an email that appears to come from your domain. Your customers won’t know the difference until it’s too late. That’s where SPF, DKIM, and DMARC come in.
These three protocols work like a security team for your email. Each one handles a different job, and you need all three to properly protect your business reputation.
What Is SPF (Sender Policy Framework)?
SPF acts like a bouncer at an exclusive club. It tells the world exactly which mail servers are allowed to send emails on behalf of your domain.
When you set up SPF, you’re essentially creating a list that says “These servers, and only these servers, can send emails from mydomain.com.” Any email claiming to be from your domain but sent from an unauthorized server gets flagged as suspicious.
Here’s how it works in practice. Let’s say someone tries to send a fake email from your domain using their personal Gmail account. The receiving email server checks your SPF record and sees that Gmail isn’t on your approved list. Red flag raised.
But SPF has one major weakness: email forwarding breaks it completely. When someone forwards your legitimate email to another address, the forwarding server becomes the new sender. Since that server isn’t on your SPF list, the email fails authentication even though it’s genuine.
That’s why SPF alone isn’t enough. You need backup.
Understanding DKIM (DomainKeys Identified Mail)
DKIM works like a tamper-proof seal on a package. Every email gets a unique digital signature that proves two things: the message came from an authorized server, and nobody changed the content during delivery.
Think of DKIM as invisible ink that only special equipment can read. Your mail server adds this signature using a private key that only you control. The receiving server uses a public key (stored in your DNS records) to verify the signature.
If someone intercepts your email and changes even one character, the signature breaks. The receiving server immediately knows something fishy happened.
Unlike SPF, DKIM survives email forwarding because the signature travels with the message. But DKIM has its own blind spot: it doesn’t check if the “From” address matches the domain that signed the email.
A scammer could send an email that appears to come from your domain in the “From” field while actually signing it with their own domain’s DKIM key. The signature would be valid, but the email would still be fake.
DMARC: The Missing Link
DMARC (Domain-based Message Authentication, Reporting & Conformance) is the quarterback that makes SPF and DKIM actually work together effectively.
DMARC connects the dots by checking something called “alignment.” It verifies that the domain in the “From” address matches the domain that passed SPF or DKIM authentication.
But DMARC’s real power lies in policy enforcement. You tell DMARC exactly what to do when an email fails authentication:
- None: Just monitor and report (perfect for testing)
- Quarantine: Send suspicious emails to spam folders
- Reject: Block fake emails completely
DMARC also sends you detailed reports about who’s sending emails using your domain. These reports help you catch both legitimate configuration issues and malicious activity.
How the Three Work as a Team
Think of email authentication like airport security. You need multiple checkpoints to catch different types of threats.
When an email arrives, the receiving server performs this security screening:
- SPF Check: Is this email coming from an authorized server?
- DKIM Check: Is the digital signature valid and unaltered?
- DMARC Check: Do the domains align properly, and what should I do if they don’t?
DMARC requires that at least one of the other protocols (SPF or DKIM) passes AND shows proper alignment. If both fail, DMARC policies kick in to protect the recipient.
This layered approach covers all the bases. Even if SPF breaks due to forwarding, DKIM can still authenticate the email. If DKIM fails for some reason, SPF might still pass.
Why All Three Are Non-Negotiable
You might think “Can’t I just use one or two?” Unfortunately, no. Each protocol plugs holes that the others can’t handle.
Here’s what happens with incomplete protection:
SPF only: Scammers can still forge your domain in the “From” address while sending from their own authenticated servers. Customers see your name and trust the email.
DKIM only: Criminals can use your domain name in emails while signing with their own valid DKIM signature. The technical authentication passes, but the email is still fraudulent.
SPF + DKIM without DMARC: You have no enforcement mechanism. Email providers might ignore your SPF and DKIM records because there’s no policy telling them what to do with failures.
The harsh reality? Without all three protocols properly configured, up to 76% of your legitimate business emails could end up in spam folders or get rejected outright.
The Business Impact Is Real
Major email providers aren’t playing games anymore. Starting in February 2024, Google and Yahoo made SPF, DKIM, and DMARC mandatory for anyone sending over 5,000 emails per day.
But compliance isn’t the only concern. Business Email Compromise (BEC) scams cost U.S. victims $2.9 billion in 2024 alone. When criminals can easily impersonate your business, your customers become targets.
Consider what’s at stake when someone spoofs your domain:
- Customer trust: People stop opening emails from your business
- Brand reputation: Your company name gets associated with scams
- Financial liability: Customers might hold you responsible for losses
- Email deliverability: Legitimate emails get blocked or filtered
One major breach can take years to recover from. Prevention costs far less than damage control.
Getting Started: Your Next Steps
Don’t let the technical details intimidate you. Most hosting providers and email services can help you implement these protocols correctly.
Start by checking your current status. Tools like MXToolbox or DMARC Analyzer can show you what records already exist for your domain.
If you’re sending business emails without proper authentication, you’re essentially driving without insurance. The question isn’t whether something will go wrong: it’s when.
For comprehensive email security guidance tailored to your business needs, our email security services can help you implement all three protocols correctly.
The investment in proper email authentication pays dividends in protected reputation, improved deliverability, and peace of mind. Your customers: and your bottom line: will thank you for taking email security seriously.
Don’t wait for a crisis to take action. Email authentication isn’t just about preventing attacks; it’s about ensuring your legitimate business communications actually reach their intended recipients.










by Charles Oropallo | May 17, 2025 | Internet, Security
 Cybercriminals are getting smarter every day. They’re not just sending those obvious “Nigerian Prince” emails anymore. Today’s scammers use sophisticated tactics that can fool even tech-savvy people.
Cybercriminals are getting smarter every day. They’re not just sending those obvious “Nigerian Prince” emails anymore. Today’s scammers use sophisticated tactics that can fool even tech-savvy people.
Let’s break down the three main types of social engineering attacks you need to know about. We’ll cover phishing, smishing, and vishing – plus some sneaky new tricks that emerged in 2025.
What’s the Difference Between Phishing, Smishing, and Vishing?
Think of these three methods as different doors criminals use to break into your digital life. Each one targets a different communication channel you use every day.
Phishing happens through email and fake websites. Scammers impersonate trusted companies like your bank or Amazon. They’ll send urgent messages claiming your account needs immediate attention. The goal? Get you to click malicious links or download infected attachments.
Smishing uses text messages and messaging apps like WhatsApp. These texts often claim your package is delayed or your account is compromised. They include suspicious links that steal your information when clicked.
Vishing involves phone calls or voicemails. Scammers pretend to be from your bank, tech support, or government agencies. They use high-pressure tactics to make you reveal passwords or account numbers over the phone.
How Phishing Really Works (It’s More Clever Than You Think)
Modern phishing emails look incredibly convincing. Scammers copy official logos, use proper grammar, and mirror legitimate company websites perfectly.
Here’s a real example: You receive an email from “PayPal” saying someone tried to access your account. The email looks authentic, complete with PayPal’s logo and formatting. It includes a link to “verify your identity.”
But when you click that link, you land on a fake PayPal login page. The moment you enter your credentials, criminals capture them. Within minutes, they’re accessing your real PayPal account.
The scary part? These fake websites often use HTTPS encryption, so you’ll see that “secure” lock icon in your browser. Don’t let that fool you – criminals can get SSL certificates too.
Smishing: Why Text Message Scams Work So Well
People trust text messages more than emails. We’re conditioned to respond quickly to texts, especially ones that seem urgent.
Smishing attacks often use shortened URLs like bit.ly links. These hide the real destination, making it impossible to see where you’re actually going. The messages create artificial urgency: “Your package will be returned if you don’t respond in 24 hours!”
Here’s what makes smishing particularly dangerous: Most people don’t have security software on their phones like they do on computers. This makes mobile devices easier targets for malicious websites and downloads.
Think about how many important accounts are linked to your phone number. Your bank, email, social media – they all send verification codes via text. Criminals know this and exploit it ruthlessly.
Vishing: The Human Touch That Breaks Down Your Defenses
Voice phishing feels the most personal and urgent. There’s something about hearing another person’s voice that makes threats feel real and immediate.
Skilled vishers study their targets beforehand. They might know your name, where you bank, or recent purchases you’ve made. This inside knowledge makes their calls incredibly convincing.
Caller ID spoofing makes these calls appear to come from legitimate numbers. Your phone might display your bank’s actual customer service line, even though the call is coming from a criminal’s burner phone.
The pressure tactics are intense. They’ll claim your account has been compromised and you need to verify information “right now” to prevent further damage. They might transfer you between different “departments” to make the scam feel more authentic.
The New Tricks Criminals Started Using in 2025
Artificial Intelligence changed the game completely. AI-powered phishing creates personalized messages that perfectly mimic your colleagues’ or friends’ writing styles. These aren’t generic scam emails – they’re tailored specifically for you.
Clone Phishing takes emails you’ve actually received before and creates malicious copies. Remember that legitimate email from your bank last month? Criminals recreate it exactly, but replace the links with dangerous ones. Since you recognize the format, you’re more likely to trust it.
Business Email Compromise (BEC) targets companies by impersonating executives. An employee receives an email that appears to come from their CEO, requesting an urgent wire transfer or asking for sensitive customer data. These attacks often don’t include any attachments – they rely purely on social manipulation.
Deepfake voice technology now lets criminals clone someone’s voice from just a few minutes of audio. They might call pretending to be your boss, using AI-generated speech that sounds exactly like them.
Red Flags That Scream “This Is a Scam”
Your gut instinct is often right. If something feels off, it probably is. Here are specific warning signs to watch for:
Urgent language designed to bypass your critical thinking. Phrases like “immediate action required,” “account will be closed,” or “respond within 24 hours” are huge red flags.
Requests for sensitive information through email or text. Legitimate companies never ask for passwords, Social Security numbers, or account details this way. They already have this information.
Generic greetings like “Dear Customer” instead of using your actual name. Real companies typically address you personally in important communications.
Shortened URLs or suspicious links. Hover over any link before clicking to see where it actually goes. Be especially wary of URLs with random characters or unfamiliar domains.
Grammar and spelling mistakes in messages from “professional” organizations. While scammers have gotten better at this, many still make obvious errors.
Your Defense Strategy: Simple Steps That Actually Work
For email phishing: Never click links in suspicious emails. Instead, go directly to the company’s website by typing their URL into your browser. If the issue is real, you’ll see it when you log into your account normally.
For smishing: Don’t click text message links from unknown numbers. If the message claims to be from a company you do business with, use their official app or website instead.
For vishing: Hang up and call back using the official number from the company’s website. Real representatives won’t mind you verifying their identity this way.
Enable two-factor authentication (2FA) on all important accounts. Even if criminals steal your password, they won’t be able to access your accounts without the second verification step.
Keep your software updated. This includes your operating system, web browser, and antivirus programs. Updates often fix security vulnerabilities that criminals exploit.
When in Doubt, Verify Through a Different Channel
Here’s the golden rule: If someone contacts you claiming there’s a problem, verify it independently. Don’t use the contact information they provide – look it up yourself.
Call your bank using the number on your debit card. Log into your accounts directly rather than clicking email links. Check with IT before responding to urgent requests from “executives.”
This simple habit will protect you from 99% of social engineering attacks. Criminals count on you responding immediately without thinking it through.
Protecting Your Business and Family
Share this information with your employees and family members. Cybercriminals often target less tech-savvy individuals to get access to business networks or family finances.
Create a family or workplace policy: Never give out sensitive information over the phone or via email without verification. Make it clear that taking time to verify suspicious requests is always acceptable.
Consider using a password manager and teaching others to do the same. This makes it much harder for criminals to access multiple accounts even if they steal one password.
Remember, you don’t have to become a cybersecurity expert to stay safe. Following these basic guidelines and trusting your instincts will keep you ahead of most scammers.
If you’re concerned about your business’s email security or need help implementing better protection policies, our email security consulting services can help you create a comprehensive defense strategy.
The key is staying informed and remaining skeptical of unsolicited contacts asking for information or immediate action. When criminals can’t pressure you into quick decisions, their tactics usually fail.










by Charles Oropallo | Dec 15, 2020 | Do-It-Yourself, Internet, Security, Technical Help, The CW Corner, Website Development, WordPress
Akismet provides a convenient and free way to protect your personal WordPress site or blog from spam.
Many times we’d like to allow comments to be left on our WordPress site. The hassle with this can be the tremendous amounts of spam that come through the forms on websites.
Akismet is a compact WordPress plugin that filters the incoming comments. It is pretty straightforward to use and pretty easy to set up as well.
Install the Akismet plugin
The first step in this process is to ensure that the Akismet plugin is installed in your WordPress website:
-
-
- Log into your WordPress website’s dashboard as an administrator
- Click on Plugins in the left dashboard navigation column
- Look and see if Akismet is listed – if it is – and it is not activated you can proceed to the Akismet Setup step below – otherwise
- Click on Add New under Plugins in the dashboard navigation column
- If you don’t see Akismet in the plugins, then in the text box to the right of the work Keyword in the row starting with Featured type in Akismet – then click on its Install Now button. Do not activate it yet.
Perform the Akismet Setup
To set up Akismet in your website, you will need an API code from the Akismet site. The first step in that process is to navigate to:
https://akismet.com/plans
This (as of the time of this writing) brings you to a page that should look similar to the screenshot below.
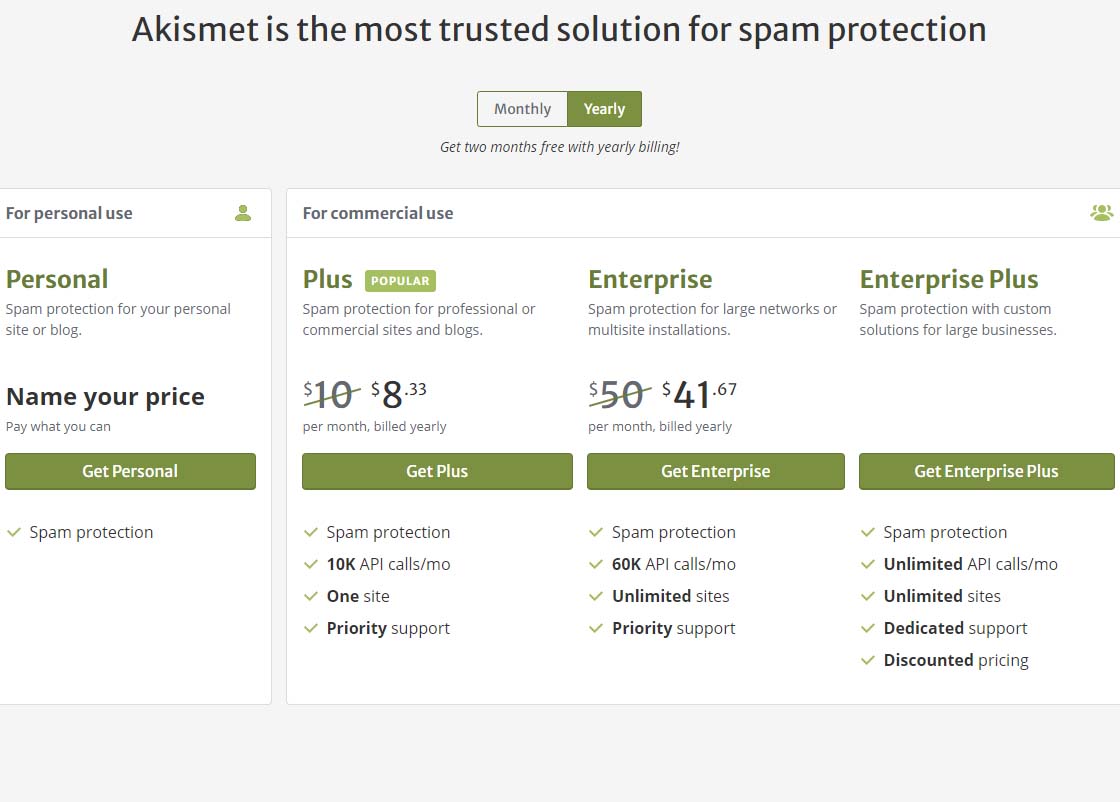 Akismet offering pricing page
Akismet offering pricing pageTo get the free version of Akismet comment spam protection, you will need to click on the Get Personal button on the above page.
Once you’ve done that, you should see a page similar to the one below. Before attempting to fill out anything on this page, we need to set that $36 / YEAR to $0 / YEAR. Click on the $36 / YEAR box and drag it to the left.
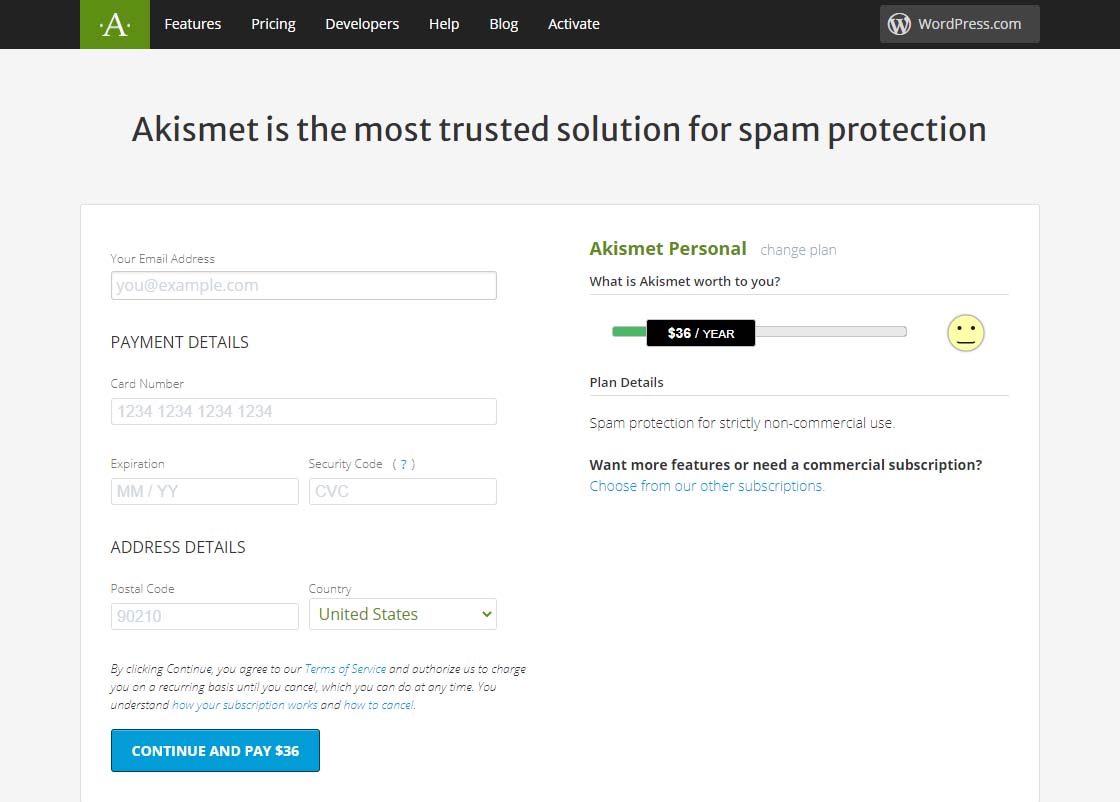 Akismet Default $36 per year page
Akismet Default $36 per year pageDragging that $36 / YEAR box to the left should change the page to display something like the one below showing 0$ / YEAR. You can also see that the information to fill in has changed.
Akismet $0 per year page
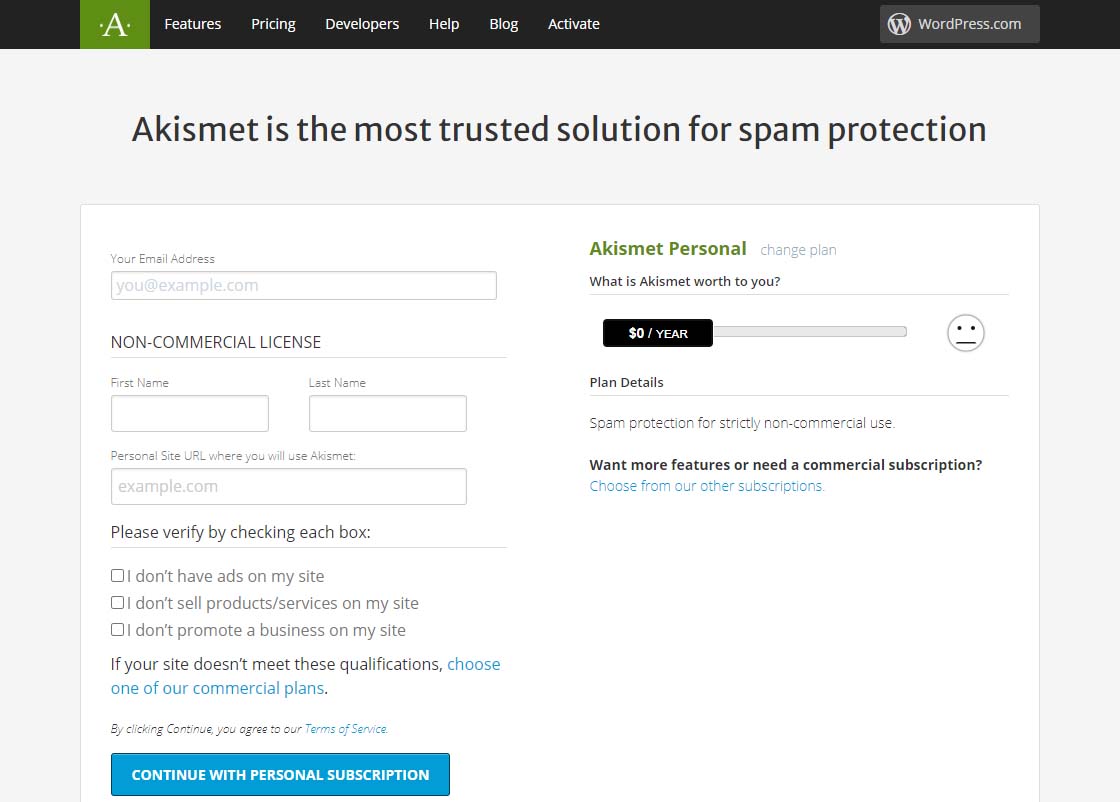 Akismet $0 per year page
Akismet $0 per year pageNow fill in the information completely. Note that you need to be able to check all three checkboxes indicating the following:
-
-
- you don’t have ads on your site
- you don’t sell products/services on your site
- you don’t promote a business on your site
If these are the case, then you will qualify for a free, personal plan.
All you have to do once you have gotten this far is follow the directions on the page below.
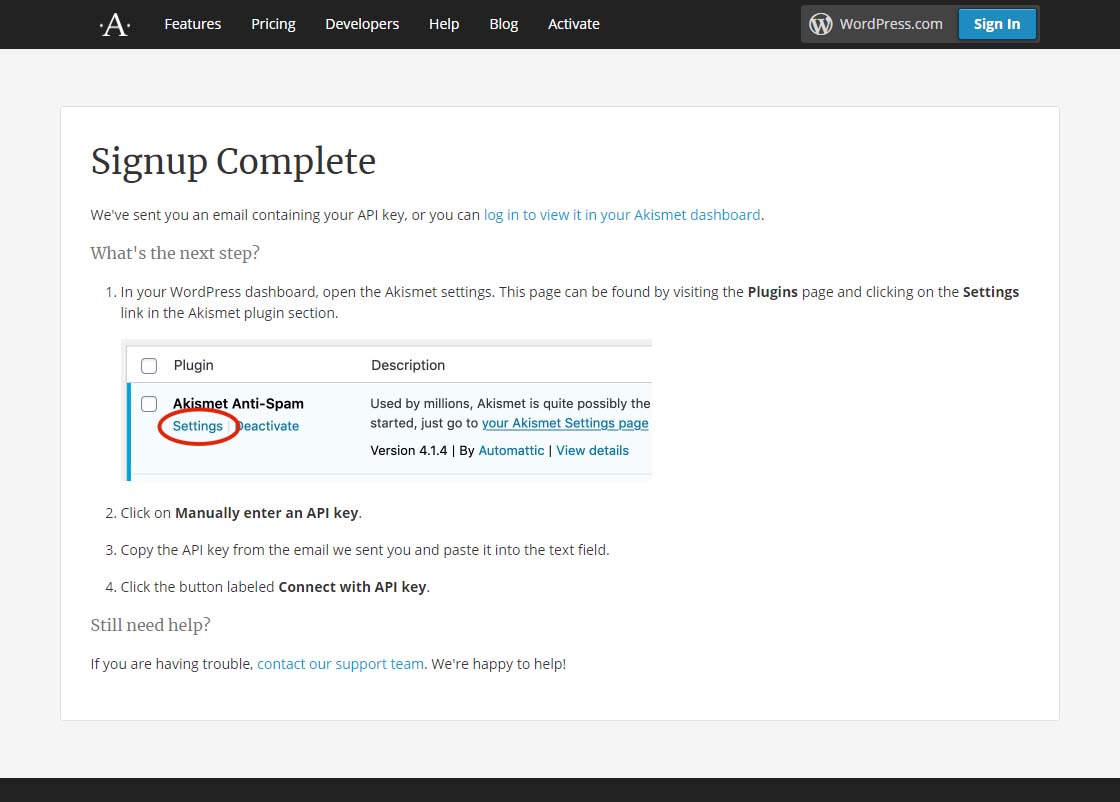 Akismet signup complete page
Akismet signup complete pageFinally, it is suggested that while on that settings page in Akismet, you can choose to show the number of approved comments beside each comment author and choose whether to show a privacy notice or not. Then just click the Save Changes button and you are on your way!










by Charles Oropallo | Oct 16, 2020 | Internet, SEO
Almost all businesses get the usual spam SEO (Search Engine Optimization) phone calls.
Recently, one of my web clients took one. As a result of such calls, she emailed me. She expressed a lot of concern about having been told very negative things about her web traffic and website operation. It sounded like he was trying to get her to spend money. Money she’d never see a return on her investment for.
High-pressure sales tactics are something I have instructed staff in all our years in business to avoid. CharlesWorks policy forbids selling clients anything they don’t need. The difficulty is that there are so many spammers and scammers out there sending the same messages that people believe them. You can tell the same lie a thousand times and it’s still a lie.
Among the thousands of websites we’ve handled, her particular business is very unique – especially during the COVID-19 epidemic. Her classes are limited regarding how many people she can have in them at any given time. I told her that she is the one who knows best what should be on her website. And she is the one who knows best what she has to offer and when she can offer it.
The nature of her business, it seemed to me, is based more on a following she has developed over time. And she is limited as to how many people at a time she can physically handle. And – much as I hate to say this – COVID is going to remain a thought in many people’s minds – at least through this upcoming winter season. Things will change when a vaccine is widely available. However, common sense dictates it will be a while before everyone generally has access to it.
I suggested she shouldn’t spend more than she absolutely has to – to just keep her business operational. Those small business owners who can stay in business through this pandemic will be the ones who do great once they reach the other side of this.
It’s troubling that someone had pressured her enough to do work on her site that she became stressed over it. Sales people who proceed with such a hard sell attitude are clearly desperate for work. Desperate people are not working with their customer’s best interest in mind. My advise is to not talk to these people.
My suggestions for dealing with these really hard line sales calls are:
- “Remove me from your calling list.” Tell them to remove you from their calling list. Once you say those words, they are supposed to do so by law. I regularly tell spammers this, and they generally don’t bother to call back.
- Block their phone number. Block their number through whatever mechanism your telephone carrier has set up to do that. I do this on a pretty regular basis with the robocalls (which are actually illegal in most cases) and take a few minutes to report them at the https://www.donotcall.gov/report.html site.
- Visit the National Do Not Call Registry. Go to https://www.donotcall.gov where you can put your phone numbers on the National Do Not Call Registry. Mine have been on this for many years.
While these suggestions don’t stop all the spam calls you’ll get, they do stop many.
Every small business owner can and should review their website. They should ensure that everything is up to date for offerings and schedules. That only costs them a few minutes. Because CharlesWorks charges for changes by the minute, those kinds of changes only incur those minutes of charges.
I hope this is helpful to you!










 Phishing attacks have become more sophisticated than ever in 2025. Cybercriminals now use AI to craft convincing emails that mimic your trusted contacts perfectly. They’re targeting small businesses more aggressively because they know you might not have enterprise-level security budgets.
Phishing attacks have become more sophisticated than ever in 2025. Cybercriminals now use AI to craft convincing emails that mimic your trusted contacts perfectly. They’re targeting small businesses more aggressively because they know you might not have enterprise-level security budgets. Think your business emails are secure? Think again. Every day, cybercriminals send millions of fake emails pretending to be from legitimate businesses. Without proper email authentication, your company name could be next.
Think your business emails are secure? Think again. Every day, cybercriminals send millions of fake emails pretending to be from legitimate businesses. Without proper email authentication, your company name could be next. Cybercriminals are getting smarter every day. They’re not just sending those obvious “Nigerian Prince” emails anymore. Today’s scammers use sophisticated tactics that can fool even tech-savvy people.
Cybercriminals are getting smarter every day. They’re not just sending those obvious “Nigerian Prince” emails anymore. Today’s scammers use sophisticated tactics that can fool even tech-savvy people.






 European Union General Data Protection Regulation Compliant
European Union General Data Protection Regulation Compliant