
by Charles Oropallo | Aug 23, 2024 | Do-It-Yourself
WordPress powers over 40% of all websites on the internet. That popularity makes it a prime target for hackers. Every day, thousands of WordPress sites get compromised because owners make simple security mistakes.
The good news? Most of these mistakes are easy to fix. You don't need to be a security expert to protect your website. You just need to know what you're doing wrong and how to fix it.
Let's dive into the seven biggest WordPress security mistakes and their solutions.
Mistake #1: Ignoring Updates (The Silent Site Killer)
Here's the harsh truth: 97% of WordPress security problems come from plugins. Yet only 30% of WordPress users have auto-updates enabled.
Think about it this way. When developers find a security hole, they release an update to fix it. The longer you wait to update, the more time hackers have to exploit that known weakness.

How to Fix It:
Enable automatic updates for WordPress core, plugins, and themes. Most hosting providers offer this feature in their control panels. If yours doesn't, consider switching to a managed WordPress host.
Check your plugins weekly. Delete any you're not using. Inactive plugins can still be exploited by hackers.
Set calendar reminders if auto-updates aren't available. Manual updates beat no updates every time.
Pro Tip: Create a staging site to test updates before they go live. This prevents your main site from breaking during updates.
Mistake #2: Using Weak Passwords and Predictable Usernames
"admin" with password "password123" isn't clever. It's dangerous. 41% of WordPress users still use weak passwords or skip two-factor authentication entirely.
Hackers use bots that test thousands of password combinations per minute. A weak password like "ADMIN123" gets cracked in seconds.
How to Fix It:
Create strong passwords with at least 12 characters. Mix uppercase, lowercase, numbers, and special characters.
Never use "admin" as your username. Choose something unique that doesn't relate to your business name.
Use a password manager like 1Password or Bitwarden. They generate complex passwords and store them securely.
Change default usernames immediately. If you already have an "admin" account, create a new administrator account with a different username, then delete the old one.
Quick Check: Can you guess your password by looking at your keyboard or personal information? If yes, change it now.
Mistake #3: Skipping Two-Factor Authentication (Your Security Backup Plan)
Passwords alone aren't enough anymore. Even strong passwords can be compromised through data breaches or phishing attacks.
Two-Factor Authentication (2FA) adds a second layer of protection. Even if hackers get your password, they still need your phone or authentication app to get in.

How to Fix It:
Install a 2FA plugin like Wordfence or Google Authenticator for WordPress.
Set up 2FA for all user accounts, especially administrators and editors.
Use an authenticator app instead of SMS when possible. Apps like Google Authenticator or Authy are more secure than text messages.
Test your 2FA setup regularly. Make sure you can access backup codes if you lose your phone.
Remember: 2FA might seem inconvenient, but it's much less inconvenient than rebuilding your hacked website.
Mistake #4: Forgetting to Back Up Your Website
"My hosting company handles backups." Famous last words from website owners who lost everything.
Hosting backups might not include all your files. They might be stored on the same server that gets hacked. Or they might be overwritten before you realize you need them.
How to Fix It:
Set up automated daily backups that include your entire website and database.
Store backups in multiple locations. Use cloud services like Google Drive, Dropbox, or Amazon S3.
Test your backup restoration process monthly. A backup that doesn't restore is useless.
Keep at least 30 days of backup history. Sometimes you don't notice problems immediately.
Use plugins like UpdraftPlus or BackWPup for automated scheduling.
Reality Check: When did you last check if your backups actually work? If you can't answer that, check today.
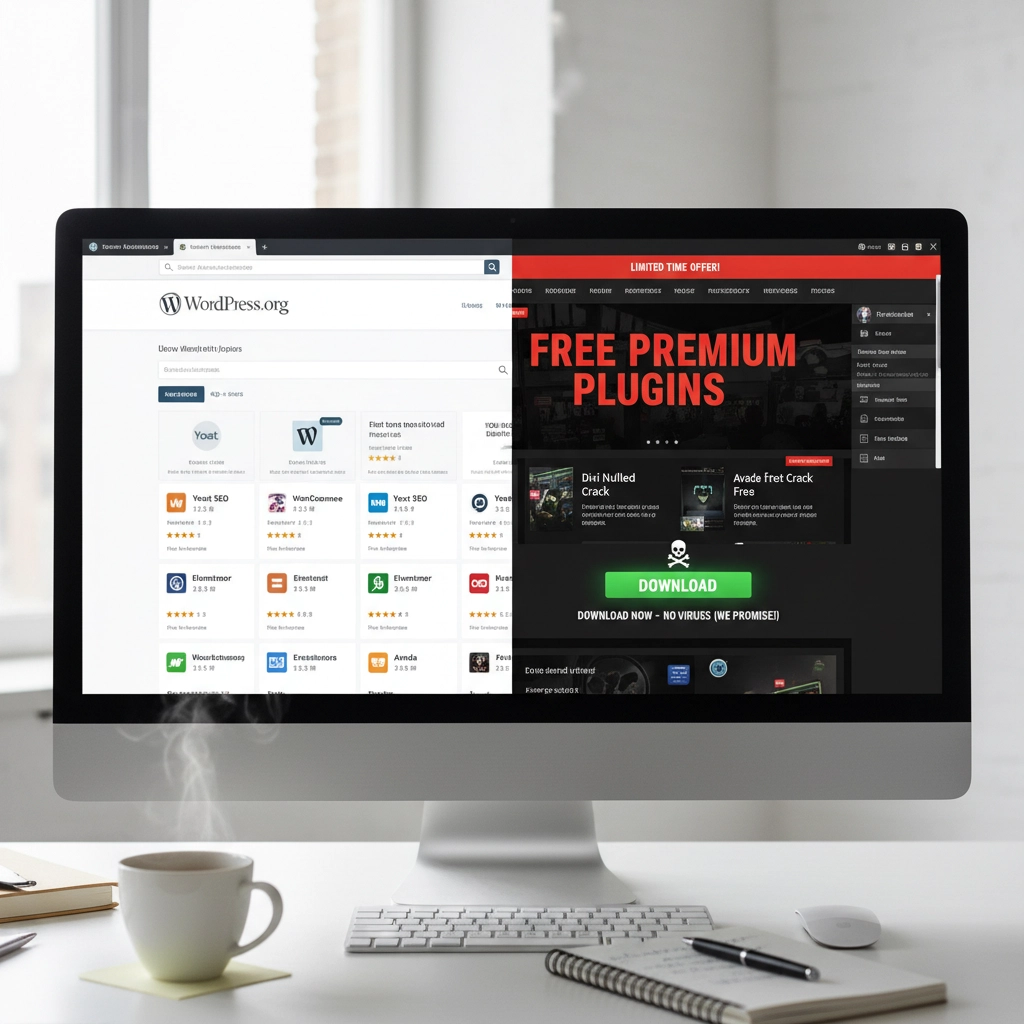
Mistake #5: Installing Themes and Plugins from Sketchy Sources
Free premium themes and plugins sound tempting. But they often come with hidden malware or backdoors that give hackers access to your site.
Even legitimate-looking themes can contain malicious code that steals user data or redirects visitors to scam sites.
How to Fix It:
Only download themes and plugins from the official WordPress repository or established developers.
Check ratings and reviews before installing anything. Look for recent updates and active support.
Research the developer. Do they have other plugins? A professional website? Good reviews?
Scan new themes and plugins with security tools before activation.
Delete unused plugins immediately. Don't just deactivate them: remove them completely.
Warning Sign: If a "premium" theme or plugin is offered free on a random website, it's probably infected with malware.
Mistake #6: Ignoring File Permissions (The Technical Blind Spot)
File permissions control who can access what on your server. Wrong permissions can let hackers read sensitive files or upload malicious code.
Most WordPress users never check their file permissions. They assume their hosting provider set them correctly. That's a dangerous assumption.
How to Fix It:
Set correct file permissions: 755 for directories and 644 for files.
Never use 777 permissions unless absolutely necessary (and change them back immediately after).
Protect your wp-config.php file with 600 permissions.
Work with your hosting provider to audit permissions if you're unsure.
Use security plugins that monitor and alert you about permission changes.
Technical Note: If file permissions sound too complex, ask your web developer or hosting support to check them for you.
Mistake #7: No Security Monitoring (Flying Blind)
Many WordPress owners only discover they've been hacked when visitors complain or Google flags their site. By then, the damage is done.
Hackers often work silently, stealing data or using your site to attack others. You need active monitoring to catch problems early.

How to Fix It:
Install security monitoring plugins like Wordfence, Sucuri, or iThemes Security.
Set up email alerts for suspicious login attempts, file changes, or malware detection.
Monitor your website traffic for unusual spikes or patterns.
Check your site regularly from different devices and browsers.
Use Google Search Console to monitor for security warnings.
Pro Tip: Set up uptime monitoring to alert you immediately if your site goes down. Services like UptimeRobot offer free basic monitoring.
Taking Action: Your Security Checklist
Security isn't a one-time task. It's an ongoing process. Here's your priority order for fixing these mistakes:
- Enable automatic updates immediately – This fixes your biggest vulnerability right now
- Change weak passwords and usernames – Use a password manager to make this easy
- Set up 2FA on all accounts – Add that crucial second layer of protection
- Configure automated backups – Your safety net for when things go wrong
- Audit your plugins and themes – Remove anything suspicious or unused
- Check file permissions – Get help if this feels too technical
- Install security monitoring – Your early warning system
Don't try to fix everything at once. Start with automatic updates and work down the list. Each step makes your site significantly more secure.
Remember: The best time to secure your WordPress site was yesterday. The second-best time is right now.
Need help implementing these security measures? Our team specializes in WordPress security and can audit your site for vulnerabilities. Contact us for a security consultation that could save your website from becoming another hacking statistic.











by Charles Oropallo | Mar 14, 2024 | Do-It-Yourself
You're paying for a website, but your local customers can't find you online. Sound familiar? Here's the truth: most web developers focus on making sites look pretty. They skip the local search engine optimization (SEO) tactics that actually get you found.
Local SEO isn't rocket science. It's a series of strategic moves that help your business appear when people search for services "near me." The best part? You can implement most of these yourself.
Let's dive into the strategies that actually move the needle for small businesses.
Your Google Business Profile Is Everything
Your Google Business Profile is the foundation of local visibility. It's free, takes 15 minutes to set up, and directly impacts your Google Maps rankings.
Think about your last local search. You probably clicked on one of the first three businesses in the map results. Those spots aren't random, they're earned through profile optimization.
Complete every section of your profile. Add your business hours, phone number, website, and services. Upload high-quality photos of your storefront, products, and team. Businesses with photos get 42% more direction requests than those without.
Post regular updates about promotions, events, or new services. Google treats active profiles as more relevant than dormant ones. Even a weekly post about your business makes a difference.

Enable messaging if your business can respond quickly. Enable appointment booking if applicable. These features signal to Google that your business is engaged and customer-focused.
NAP Consistency Rules Everything
NAP stands for Name, Address, Phone Number. This information must be identical everywhere your business appears online. Everywhere means your website, social media, directories, and citations.
Here's what happens when your NAP is inconsistent: Google doesn't trust your business information. Confused search engines don't rank confused businesses highly.
Create a master document with your exact business information. Use "Street" instead of "St." Use your local phone number, not a toll-free number. If your business name is "Joe's Coffee," don't call it "Joe's Coffee Shop" anywhere else.
Check your NAP across these platforms: Google Business Profile, Yelp, Facebook, Yellow Pages, Better Business Bureau, and industry directories. Fix any inconsistencies immediately.
One formatting tip that saves headaches later: always use your business address exactly as it appears on your Google Business Profile. This becomes your standard format everywhere else.
Local Keywords Are Your Best Friend
Local keywords help the right people find your business. These aren't complicated, they're simply your services plus your location.
Examples include "dentist in Portland," "pizza delivery Chicago," or "car repair near me." Research what your customers actually search for using Google's Keyword Planner or simply by typing your services into Google and seeing the autocomplete suggestions.
Create separate pages for different service areas if you serve multiple locations. A plumbing company serving three towns should have dedicated pages for each area. Each page should include local landmarks, neighborhood names, and area-specific information.

Don't stuff keywords unnaturally into your content. Write for humans first, search engines second. A sentence like "Our Chicago pizza delivery service delivers pizza in Chicago" sounds robotic and hurts more than it helps.
Instead, write naturally: "We deliver fresh pizza throughout Chicago's downtown area, including the Loop and River North neighborhoods."
Mobile Optimization Can't Be Optional
Sixty percent of local searches happen on smartphones. Google uses mobile-first indexing, meaning they primarily look at your mobile site to determine rankings.
Your website must load quickly on phones. Compress images, choose a fast hosting provider, and avoid heavy plugins that slow loading times. A three-second delay can lose 53% of mobile visitors.
Make buttons large enough for thumbs. Avoid tiny links or navigation elements that frustrate mobile users. Test your site on different devices and screen sizes.
Eliminate pop-ups that cover mobile screens. Google penalizes sites with intrusive mobile pop-ups. If you must use pop-ups, make them easy to close and ensure they don't block important content.
Check your mobile-friendliness with Google's Mobile-Friendly Test. It's free and shows exactly what needs fixing.
Customer Reviews Drive Everything
Reviews influence both customers and search rankings. Google considers review quantity, frequency, and responses when determining local rankings.
Ask satisfied customers for reviews. Don't be pushy, but don't be shy either. A simple request after completing good work often works: "If you're happy with our service, a quick Google review would really help our small business."
Respond to every review, positive and negative. Thank customers for positive reviews. Address negative reviews professionally and offer to resolve issues offline.

Here's a template for negative review responses: "Thanks for your feedback, [Name]. We apologize for your experience and would like to make this right. Please call us at [phone] so we can discuss this further."
Never ignore reviews. Silent businesses look unengaged to both customers and Google.
Local Directories Still Matter
Getting listed on local directories builds credibility and provides valuable backlinks to your website. Start with major directories like Yelp, Yellow Pages, and your local Chamber of Commerce website.
Industry-specific directories matter too. Restaurants should be on OpenTable and TripAdvisor. Contractors should be on Angie's List and Home Advisor.
Ensure your NAP information is consistent across all directories. Inconsistent listings hurt more than they help.
Don't pay for directory submissions unless you're certain they're legitimate. Many "directory submission services" are scams that list your business on low-quality sites.
On-Page SEO With Local Focus
Optimize your website content for local search by including location-based keywords naturally throughout your pages.
Your homepage should mention your primary service area early and often. Include your city or region in your title tag, meta description, and main headings.
Create location-specific content that provides value. A home improvement company could write about local building codes, weather considerations, or neighborhood characteristics.
Add your address to your website footer. Include local landmark references in your content. Mention nearby businesses, events, or community involvement.

Don't forget about image optimization. Name your photos with descriptive, location-specific filenames like "chicago-pizza-restaurant-interior.jpg" instead of "IMG_1234.jpg."
Advanced Local SEO Tactics
Geo-tag your images when uploading to your website and social media. This embeds location data that helps search engines understand your business location.
Build relationships with other local businesses for natural backlink opportunities. Sponsor local events, join community organizations, or participate in local business associations.
Create Google Posts regularly through your Google Business Profile. These mini-blog posts appear in your knowledge panel and show Google that your business is active.
Monitor your online mentions using Google Alerts. Set up alerts for your business name to catch new reviews, mentions, or potential NAP inconsistencies.
Consider local schema markup on your website. This structured data helps search engines understand your business information more clearly.
Common Mistakes That Kill Local Rankings
Buying fake reviews destroys credibility and violates Google's guidelines. Focus on earning authentic reviews through excellent service.
Using inconsistent business names across platforms confuses search engines. Stick to one version of your business name everywhere.
Ignoring negative reviews makes problems worse. Address concerns professionally and publicly to show potential customers how you handle issues.
Creating multiple Google Business Profiles for one location results in suspension. Google allows one profile per location, period.
Measuring Your Local SEO Success
Track your Google Business Profile insights to see how customers find you. Monitor calls, website clicks, and direction requests.
Use Google Search Console to see which local keywords drive traffic to your website. Focus your efforts on keywords that generate actual business.
Check your local rankings monthly for your most important keywords. Tools like BrightLocal or simply searching on different devices can show your position.
Most importantly, track actual business results. More calls, appointments, or walk-ins matter more than rankings alone.
Local SEO isn't complicated, but it requires consistency and attention to detail. Start with your Google Business Profile, fix your NAP consistency, and build from there. Your local customers are searching for your services right now( make sure they can find you.)










by Charles Oropallo | Feb 27, 2024 | Do-It-Yourself

Think your WordPress site is secure? You might be shocked to learn that 97% of WordPress security problems stem from plugin vulnerabilities alone. Even worse, hackers know exactly which mistakes you're making, and they're counting on you to keep making them.
Don't panic. Most WordPress security breaches happen because site owners unknowingly leave the digital equivalent of their front door wide open. The good news? These mistakes are completely preventable once you know what to look for.
Let's dive into the seven most dangerous security mistakes that make your WordPress site an easy target for cybercriminals.
1. Running Outdated or Inactive Plugins
Here's a scary statistic: only 30% of WordPress users have auto-updates enabled on their websites. That means 70% are sitting ducks for hackers who specifically target outdated plugins.

How Hackers Exploit This: Cybercriminals use automated scanning tools that crawl the web looking for sites running vulnerable plugin versions. When they find one, they already have the exploit code ready to go. It's like leaving your house key under the doormat with a sign pointing to it.
Take the 2023 vulnerabilities in WP Fastest Cache and Essential Add-ons for Elementor. Thousands of websites running outdated versions became instant targets. Hackers didn't need to be clever, they just needed to find sites that hadn't updated.
The Fix: Enable automatic updates for plugins whenever possible. If you prefer manual control, check for updates weekly. More importantly, delete any plugins you're not actively using. Inactive plugins are still attack vectors that hackers love to exploit.
2. Using Weak Passwords and Skipping Two-Factor Authentication
Here's a reality check: 41% of WordPress users don't use strong passwords or two-factor authentication (2FA). If your admin password is "password123" or your business name plus the year, you're basically sending hackers an invitation.
How Hackers Exploit This: Brute force attacks are the digital equivalent of trying every key until one opens the lock. Hackers use bots that attempt thousands of login combinations per minute. Since WordPress allows unlimited login attempts by default, these bots can run 24/7 until they crack your password.
Once they're in, they own your site. Customer data, financial information, email addresses, everything becomes theirs to sell or exploit.
The Fix: Use passwords that are at least 12 characters long with a mix of letters, numbers, and symbols. Better yet, use a password manager to generate unique passwords for every account. Enable 2FA immediately, Google's research shows it stops 100% of automated bot attacks.
3. Installing Plugins and Themes from Sketchy Sources
Free premium themes and plugins sound tempting, right? Those "nulled" versions of expensive plugins seem like a steal. Here's the truth: if something seems too good to be true, it probably contains malware.
How Hackers Exploit This: Malicious developers embed backdoors directly into these "free" premium plugins. The moment you install them, hackers have a secret entrance to your site. Some plugin viruses are designed to automatically infect every other plugin and theme on your installation, spreading like wildfire through your entire WordPress setup.
These backdoors often go undetected for months, giving hackers plenty of time to steal data, inject spam links, or use your server for cryptocurrency mining.
The Fix: Stick to plugins and themes from WordPress.org, reputable commercial developers, or well-established marketplaces. Yes, you might pay more upfront, but it's infinitely cheaper than dealing with a hacked website.
4. Ignoring File Permissions
File permissions might sound technical, but they're basically your site's security guard. When configured incorrectly, they're like having a security guard who lets anyone walk into your building.
How Hackers Exploit This: Loose file permissions allow attackers to access sensitive files they shouldn't see. Once they have limited access, they can often escalate their privileges and gain control of critical system files. It's like giving someone permission to use your bathroom, and they end up with keys to your entire house.
With proper access, hackers can modify your site's code, steal database information, or install persistent backdoors that survive even when you clean up other security issues.
The Fix: Follow the principle of least privilege. Files should be set to 644 permissions, directories to 755. Your wp-config.php file should be 600. If these numbers look like gibberish, ask your hosting provider to audit your file permissions.
5. Procrastinating on WordPress Updates
Those update notifications aren't suggestions: they're security bulletins. Every WordPress update includes patches for newly discovered vulnerabilities. When you ignore them, you're essentially leaving known security holes open for hackers to exploit.
How Hackers Exploit This: WordPress developers openly publish what each security update fixes. This creates a roadmap for hackers who can easily identify which sites haven't updated and target the specific vulnerabilities that remain unpatched.
It's like fixing a broken lock on your front door but announcing to the neighborhood exactly when the repair will happen. Unpatched sites become obvious targets.
The Fix: Update WordPress core, plugins, and themes as soon as updates become available. Schedule a weekly maintenance window to check for and install updates. Most hosting providers offer staging environments where you can test updates before applying them to your live site.
6. Skipping Backups and Security Monitoring
Not having backups is like driving without insurance: you'll only realize how crucial it is when disaster strikes. Similarly, running a WordPress site without security monitoring is like closing your eyes and hoping nothing bad happens.
How Hackers Exploit This: Without backups, when (not if) your site gets compromised, you have no clean version to restore. Hackers know this, which is why some attacks are designed to corrupt or encrypt your existing files, leaving you with no recovery options.

Without security monitoring, attacks can run undetected for weeks or months. During this time, hackers can steal customer data, inject malicious code, or use your site to attack other websites.
The Fix: Set up automated daily backups stored off-site (not on the same server as your website). Install a security plugin that monitors file changes, login attempts, and suspicious activity. For critical business sites, consider our email security services that include comprehensive monitoring.
7. Installing Software from Unknown Repositories
This mistake often flies under the radar but can be the most dangerous. Installing plugins or themes from forums, random websites, or commercial repositories outside the WordPress ecosystem introduces unknown code into your installation.
How Hackers Exploit This: Unlike WordPress.org plugins that undergo community scrutiny, third-party sources may lack any security review process. These repositories are often intentionally compromised or simply don't have the resources to properly vet code.
Hackers exploit this by creating legitimate-looking plugins or themes that contain hidden malware. Once installed, these give attackers automatic access to your site without needing to break in through other methods.
The Fix: Stick to WordPress.org for free plugins and themes. For premium options, buy directly from the developer or established marketplaces like CodeCanyon. Never download "nulled" versions of paid plugins: they're almost always infected with malware.
Your Next Steps
WordPress security isn't rocket science, but it does require consistent attention. Start by auditing your current setup against these seven mistakes. Update everything, remove unused plugins, strengthen your passwords, and enable 2FA.
Remember, hackers are counting on you to make these mistakes. Don't give them the satisfaction. A few hours of security maintenance now can save you weeks of cleanup later: not to mention the potential loss of business and customer trust.
Need help securing your WordPress site? We specialize in helping businesses protect their digital assets without the technical headaches. Your website is too important to leave to chance.











by Charles Oropallo | Dec 17, 2023 | Do-It-Yourself
Let's be honest, you didn't start your business to become a cybersecurity expert. You've got products to sell, customers to serve, and a bottom line to protect. But here's the thing: spending hours wrestling with complicated security tutorials isn't the answer.
The good news? Website security doesn't have to eat up your entire weekend. With these seven practical hacks, you can lock down your site without needing a computer science degree. These aren't theoretical tips, they're battle-tested strategies that take minutes to implement but provide months of protection.
Think of this as your security cheat sheet. No fluff, no technical jargon, just straight-forward steps that actually work.
1. Turn On Multi-Factor Authentication (MFA) Everywhere
Here's your first quick win: enable multi-factor authentication on every account that touches your business. This means requiring two forms of identification, like your password plus a code sent to your phone, before anyone can access your systems.
Why does this matter? Even if hackers crack your password, they still can't get in without that second verification step. It's like having a deadbolt and a security chain on your front door.

Set this up on your website admin panel, email accounts, social media profiles, and any business applications you use. Most platforms make this incredibly easy, usually just a toggle switch in your security settings.
Don't skip this step because it seems like a hassle. The extra 30 seconds during login is nothing compared to the weeks you'd spend recovering from a breach.
2. Get That SSL Certificate Installed (And Keep It Updated)
If your website URL doesn't start with "https://", you're broadcasting to the world that your site isn't secure. Visitors see those dreaded "Not Secure" warnings, search engines penalize your rankings, and hackers see an easy target.
An SSL certificate encrypts data between your website and visitors. It's like putting your conversation in a locked briefcase instead of shouting it across a crowded room.
Most hosting providers offer SSL certificates for free or under $20 per year. If you're not sure whether yours is installed correctly, just look at your address bar. You should see a little lock icon next to your domain name.
Pro tip: Set a calendar reminder to check your SSL certificate renewal date. An expired certificate means your site goes back to showing security warnings, not exactly the professional image you want.
3. Schedule Monthly 15-Minute Security Checkups
Here's where most business owners go wrong: they set up security once and forget about it. That's like installing smoke detectors and never checking the batteries.
Instead, block out 15 minutes each month for a quick security review. During this time, scan for suspicious login attempts, check for broken or modified pages, and verify your backups are working.
You don't need fancy tools for this. Most content management systems have built-in activity logs that show recent changes and user logins. Look for anything unusual, logins from strange locations, files you didn't create, or pages that suddenly load slowly.
Think of this as preventive maintenance for your digital storefront. Catching problems early means fixing them takes minutes instead of days.
4. Enable Automatic Updates (Yes, Really)
"But what if an update breaks my site?" This fear keeps many business owners running outdated, vulnerable software. Here's the reality: the risk of a hacker exploiting an old security hole far outweighs the small chance an update causes problems.
Software updates aren't just about new features, they're about patching security vulnerabilities that hackers actively target. Running outdated software is like leaving your keys in an unlocked car.
Enable automatic updates for your website's core software, plugins, and themes. If your platform doesn't support automatic updates, set weekly calendar reminders to install them manually.
Still worried about updates breaking things? That's what backups are for (more on that in tip #6). The peace of mind from staying current on security patches is worth the occasional minor glitch.
5. Implement a Real Password Policy
"Password123!" doesn't count as secure, no matter how many exclamation points you add. Weak passwords are like having a "Welcome" mat for hackers.
Create a simple password policy for your team: minimum 12 characters, mix of letters/numbers/symbols, and no reusing passwords across accounts. Better yet, use a password manager to generate and store complex passwords automatically.

Think about what's connected to your email accounts, your website admin panel, and your business applications. One compromised password can unlock everything. Don't make it easy for the bad guys.
If remembering complex passwords feels overwhelming, password managers like Bitwarden or LastPass do the heavy lifting. They generate random passwords and fill them in automatically, security made simple.
6. Set Up Automatic Backups and Vulnerability Scanning
Imagine losing months of work because your website got hacked or your server crashed. Now imagine getting everything back with the click of a button. That's the power of automatic backups.
Configure daily backups of your entire website: files, database, everything. Store these backups off-site, not on the same server as your website. Many hosting providers include this service, or you can use plugins that backup to cloud storage.
Pair this with vulnerability scanning. Services like Sucuri or Wordfence automatically check your site for malware, outdated software, and security holes. They send email alerts when they find problems, so you can fix issues before hackers exploit them.
The goal isn't to never have problems: it's to bounce back quickly when they happen. Automatic backups and scanning give you that resilience without ongoing effort.
7. Audit Your Plugins and Third-Party Tools
Your website is only as secure as its weakest link. That forgotten plugin you installed two years ago might be full of security holes, giving hackers a backdoor into your site.
Conduct a quarterly audit of every plugin, integration, and third-party tool connected to your website. Ask yourself: "Do I actually use this? Is it from a reputable developer? When was it last updated?"
Delete anything you don't actively use. For the tools you keep, enable security notifications so you know about vulnerabilities immediately. Subscribe to security blogs or newsletters from your plugin developers.

This includes seemingly harmless additions like social media widgets, analytics tools, and contact forms. Each one represents a potential entry point. The fewer doors you have, the fewer you need to guard.
The Bottom Line: Security as a Business Habit
These seven hacks work because they create multiple layers of protection without requiring constant attention. You're not trying to become a security expert: you're building good habits that run on autopilot.
The key is treating security like any other business routine. You wouldn't skip payroll or forget to pay rent. Website security deserves the same consistent attention.
Start with multi-factor authentication and SSL certificates: these give you the biggest security boost for the least effort. Then work through the other tips over the next few weeks.
Your future self will thank you when you're running a secure, professional website instead of dealing with the aftermath of a security breach. And your customers will appreciate knowing their information is safe in your hands.
Need help implementing any of these security measures? Our team at The CharlesWorks Corner specializes in making website security simple and manageable for busy business owners. Don't let security concerns keep you up at night when practical solutions are just a click away.










by Charles Oropallo | Aug 21, 2022 | Do-It-Yourself, The CW Corner
Many costs for energy have risen in recent months. Here in the Northeast our electric bills just suffered a 110% hike. For the math challenged: that’s more than doubled!! The change was this:
- OLD RATE pre 8/1/2022: 10.669¢ per kWh (kilo or thousand watt hours)
- NEW RATE post 7/31/2022: 22.566¢ per kWh
I operate CharlesWorks from my home. So this applies to home services. We run many web servers and computers here so the electric rate increase resulted in an immense change. Saving money on electric is important to everyone.
Saving Money on Electric through Research
The biggest hassle I ran into was simply understanding my electric bill. The monthly electric bill has gotten quite complex. There are two basic parts to my electric bill:
- Supplier: This is the part of the electric bill that just increased from 10.669¢ to 22.566¢ per kWh. This is the part that we can shop around for better pricing on.
- Delivery: This is the part of the electric bill that will remain constant. This seems the most complicated because there are a number of components (8 on my bill) listed in this. The total on my bill for these delivery charges ended up at 12.21¢ per kWh. Whatever this total amount is on your bill should not change should you switch suppliers. So this cost should remain the same.
I did a lot of research on this. Hopefully this will save you the hassle of researching. Ultimately, I discovered that the process is, like many things we study, learn and practice, quite straightforward.
To switch my electric supplier there were a couple of prerequisites I needed assurance of:
- That my electric bill was actually going to go down. Sounds over-simplistic but I am cautious when it comes to ongoing expenses.
- That there were no cancellation fees should I change my mind if the power rate were to lower. I’ve not really seen that happen before – but just in case.
Moving to Direct Energy
 I decided to switch to Direct Energy. After a lot of researching around and talking to several others, I found they were the best of all worlds:
I decided to switch to Direct Energy. After a lot of researching around and talking to several others, I found they were the best of all worlds:
- LOW RATE: Direct Energy offers the lowest kilowatt hour rate at 16.59¢ kWh which was the lowest I could find.
- NO CANCELLATION FEE: Direct Energy offers switching to a 36 month contract with no cancellation fee should I move away. Most other companies I researched imposed at least a $100 cancellation fee.
- REFERRAL FEE: Direct Energy offers a referral fee. If you refer someone else to them who signs up they will give you a $50 referral fee. You can’t go wrong there. Mine is http://www.directenergy.com/refer-a-friend/raf/D866981 and if you click on that you can get started saving like I did.
- $50 FOR SIGNUP: At the time of this article Direct Energy is offering a $50 Visa Prepaid Card for signing up using a friend’s referral – so you can get this by using my referral code.
Here is the information you will need to switch over to Direct Energy. You should have this info handy when you sign up. It is all on your current electric bill:
- ACCOUNT NUMBER: You’ll need your current electric or gas bill Account Number. On my bill it was listed on the upper left corner of the first page.
- CUSTOMER NAME KEY: You’ll need what is called the Customer name key. On my bill it is 4 letters located in the upper left corner of the second page of the electric bill.
So switching really was a no brainer in light of the worst PSNY/Eversource electric power rate increase I have ever seen.
Act Now
I can’t say how long this rate or particular deal will remain in effect. I can only encourage you to act now while the offer is happening.
Just CLICK HERE to take advantage of this offer while it lasts!










by Charles Oropallo | Jun 30, 2022 | Do-It-Yourself, Email, Internet, Passwords, Security, Website Updates, WordPress
We at CharlesWorks are often asked by our web clients if their site is protected from malware and getting hacked. They also want to know if there site IS hacked, whether there be a charge to fix it.
The totally hack-proof website
The totally hack proof website has no access to it. So it’s not connected to the Internet. No one can view it. Such a website doesn’t sound like its of much use if no one can see it.
So, let’s agree that it is unrealistic to believe that a publicly accessible website can be totally hack-proof. Any website that is accessible via the public Internet is consistently subjected to attempts to break into it. Believe it or not, that’s the norm as opposed to the anomaly.
That being said, however, there ARE things you can do to mitigate website hacks. I have to stress the word mitigate here. Mitigation is defined as the action of reducing the severity, seriousness, or painfulness of something.
Site hacks are based on odds
My goal here is to simply remind you of what you most likely already know: that we can reduce the probability – the odds – of your site being hacked. We at CharlesWorks want that probability to be so low that it hopefully it doesn’t ever happen to you.
The major hacking causes
I have been operating CharlesWorks since 1998. In my experience, there appear to be two major reasons why sites get hacked:
-
- The access credentials/passwords have been compromised.
- The software that operates them wasn’t kept up to date.
Lets take a look at each of these below.
Compromised Access Credentials
Compromised passwords and bad actors gaining access to website login credentials is the major reason we see sites hacked. Think about this in terms of your car. You could have alarms on it. But if you make a copy of your car key and give it to someone, they can do whatever they like with the car. Whether its a drive along the beach or to rob a bank, your car is theirs to use with the key you gave them. Credentials – log in and passwords – work pretty much the same way.
CharlesWorks has many clients who want to be able to do things themselves. We are strong proponents of doing it yourself when it’s feasible and convenient. This is especially true for adding posts or page materials. It also makes sense when making other changes or modifications to your site. It is, after all, YOUR website.
However, many people fall prey to phishing schemes. Directly or indirectly, they usually end up tricked into giving out their website access credentials (as well as credentials to everything else they own). This is especially true if your email account is hacked and the hackers are able to access emails containing your website’s (and other) login credentials.
This problem is exacerbated if you have shared your website’s administrative or other access with others. Think of your emails containing various authorizations or login information as a potential weak link in a chain. If you have shared that information with others you have now created more weak links. This increases the odds of a potential compromise.
One of the best ways to mitigate these situations is to change your site’s access passwords so they are different than those possibly stored in your emails. And, to hope that anyone you may have shared your website access with has done the same.
Obviously, should site access be gained in such a manner, it would be your burden to have the site restored. I’ll expound upon this a little more at the end of this article.
Out of Date Security/Software Updates
Malware and virus protection on home computers operates a little differently than the same types of protection on servers. Website servers operate in the publicly accessible Internet. This results in many more entry points for potential issues. There are a number of very standard server protections available (which we utilize here at CharlesWorks).
After bad actors getting (or guessing) your passwords, the next major reason sites get hacked surrounds unapplied security updates and other software update issues. At CharlesWorks we mitigate such issues by running anti-malware software on our servers. Also, WordPress sites hosted on our servers are kept up to date automatically via automatic updating of the WordPress core as well as automatic updating of the the website’s plugins and themes.
There are literally thousands of individual pieces of software that must work in unison to operate most websites. These are developed by many more thousands of developers around the world. Unfortunately, no company can guarantee that a website will never get hacked. They can only mitigate security compromises and hope against the worst.
Restoring your Website
Regardless of which of the two situations above may have led to your website’s issues, your website will most likely need to be restored. That’s because after a bad actor or a hack back doors into the site will most likely have been installed for the bad actors to gain access again.
Many Internet companies claim to have automatic backups. In most of those, those backups are accessible to the user in their account. If the account is hacked, how safe do you suppose that is?
Some Internet companies delete and account upon a website being hacked. In those cases I have seen many left with no website or backup as a result.
What I believe is most important regarding this topic is the manner in which our WordPress sites are backed up every day for 30 days. Our backups are made to separate servers – external to those your the site operates on. For security reasons, the site administrators do not have access to these backups. So even with a site administrator’s compromised passwords there is no access to the backups. With these backups we can usually restore an average site in about 10-30 minutes if it needs restoring. And we can go back as far back as 30 days. We would only bill our web client for the 10-30 minutes (again – for an average website) which results in only a minor charge to restore it. Note that some websites are extremely large and require much more time to restore but these are very rare).
In my experience running CharlesWorks since 1998, we’ve built and handled more than 5,000 websites. At this point in time, I do not recall the last time a website we built and totally maintained was hacked (unfortunately I recall several instances of sites maintained by others that failed to ensure the site was updated and/or had their passwords compromised).
Sites getting hacked for out of date software happens far less frequently (if at all) when security updates are kept up to date and bad actors are kept out.
I hope this helps you understand a little more about this topic.










by Charles Oropallo | Jul 4, 2021 | Do-It-Yourself, Security, The CW Corner, Website Development, Website Updates
Here we are at the 4th of July of 2021 already! The loss of life suffered in 2020 was horrendous. Yet there are people who still do not think in terms of helping their fellow citizens – and themselves – by being vaccinated. The vaccine misinformation mills are in full production.
So think about this: Exactly who benefits when we don’t vaccinate? When more of us are ill and can’t work, the economy suffers. There is no way the government wants that. They want us to all work so they can collect taxes from our labor. Enemies of America benefit when we don’t vaccinate. Who benefits when we do? We all benefit. The economy will return to normal – as will our lives.
At CharlesWorks we all chose to be vaccinated. Each of us employed here cares about ourselves and our clients. So when you make an appointment with us in person you can at least rest assured we have taken steps indicating we care about you.
The CharlesWorks policy is that the COVID unvaccinated need not apply. That is one of the many ways we show we care about others.
Vaccination will help us return to normalcy. It is a small thing to do. It is the patriotic thing to do. It is the right thing to do.










by Charles Oropallo | Jan 3, 2021 | Do-It-Yourself, Technical Help, The CW Corner, Website Development, WordPress
I wanted to create a custom HTML code function, so made one that will generate a line feed. I tested it to neaten up the output from my favorite WordPress statistics plugin: WP-Statistics by Verona Labs.
This shortcode gives the ability to add line feeds to WordPress page, post or report outputs to improve their readability. The function can easily be modified to generate any HTML output by doing this:
- rename “newline” in the “add_shortcode” line to whatever you’d like the shortcode to be named
- adjust the HTML code inside the quotes in the “return” line
In this example, we’ll create the line break shortcode.
Creating the Line Break Shortcode
Adding shortcodes in WordPress is easily accomplished by simply inserting the appropriate coding for the shortcode into your child theme’s functions.php file.
Note: Child themes should always be used. Changes made directly to the parent theme’s files are usually overwritten each time the parent theme is updated.
To add the code, first back up your site and then do the following:
- Log into the WordPress Dashboard as an administrator
- Navigate to Appearance > Theme Editor
- Select Theme Functions (functions.php) under Theme Files in the right column
- Add the short function code lines below
/* -- Start of line breaks shortcode --*/
function line_break_shortcode() {
return '<br />';
}
add_shortcode( 'newline', 'line_break_shortcode' );
/* -- End of line break shortcode --*/
Adding Line Breaks
Once the code has been added to your functions.php file, all you have to do is add the
shortcode in your text to generate a line feed at that point. The beauty of doing this as a shortcode is that it can be inserted in places that do not normally allow you to add them – like in the email output of the WP-Statistics plugin.
Note: When testing your output from the WP-Statistics plugin, there is a convenient feature that allows you to send output every minute to see what you will be sending. As a rule I normally have the report set to send daily.
A Working Example
There were a couple of WP-Statistics report items that were of particular interest to me. One is the last post date. This is handy as a reminder when one should add one or more posts to a site – especially a blog – so the site content doesn’t appear stale (or as an alternative, simply do not show blog post creation dates). Even if you are not displaying the post dates on the site, it is good to know when you last posted something.
An example of the report pattern I used was this (note that in some WordPress themes the “[” and “]” characters in the example below display as repeated – there should only be one “[” opening shortcode character and one “]” closing shortcode character surrounding the shortcode itself when you use it):
WP Statistics report for https://CWCorner.com WordPress site:
[newline]
_______________________________________________
[newline]
[newline]
Last post date: [wpstatistics stat=lpd]
[newline]
Total Site Posts: [wpstatistics stat=postcount]
[newline]
Total Site Pages: [wpstatistics stat=pagecount]
[newline]
Total Site Users: [wpstatistics stat=usercount]
[newline]
Online Users at Report Time: [wpstatistics stat=usersonline]
[newline]
_______________________________________________
[newline]
[newline]
Today's Visitors so far: [wpstatistics stat=visitors time=today]
[newline]
Today's Visits so far: [wpstatistics stat=visits time=today]
[newline]
Yesterday's Visitors: [wpstatistics stat=visitors time=yesterday]
[newline]
Yesterday's Visits: [wpstatistics stat=visits time=yesterday]
[newline]
_______________________________________________
[newline]
[newline]
Total Visitors: [wpstatistics stat=visitors time=total]
[newline]
Total Visits: [wpstatistics stat=visits time=total]
[newline]
_______________________________________________
[newline]
[newline]
End of WP Statistics Report.
[newline]
I used the underline characters to separate various parts of the output for clarity. This report pattern generated a nicer, more readable report that even looked great when viewing it on my cell phone.
While I initially added this function as a way to neaten up the output of the WP-Statistics email report – the function should work just about anyplace in WordPress except in the PHP coding itself.










by Charles Oropallo | Dec 15, 2020 | Do-It-Yourself, Internet, Security, Technical Help, The CW Corner, Website Development, WordPress
Akismet provides a convenient and free way to protect your personal WordPress site or blog from spam.
Many times we’d like to allow comments to be left on our WordPress site. The hassle with this can be the tremendous amounts of spam that come through the forms on websites.
Akismet is a compact WordPress plugin that filters the incoming comments. It is pretty straightforward to use and pretty easy to set up as well.
Install the Akismet plugin
The first step in this process is to ensure that the Akismet plugin is installed in your WordPress website:
-
-
- Log into your WordPress website’s dashboard as an administrator
- Click on Plugins in the left dashboard navigation column
- Look and see if Akismet is listed – if it is – and it is not activated you can proceed to the Akismet Setup step below – otherwise
- Click on Add New under Plugins in the dashboard navigation column
- If you don’t see Akismet in the plugins, then in the text box to the right of the work Keyword in the row starting with Featured type in Akismet – then click on its Install Now button. Do not activate it yet.
Perform the Akismet Setup
To set up Akismet in your website, you will need an API code from the Akismet site. The first step in that process is to navigate to:
https://akismet.com/plans
This (as of the time of this writing) brings you to a page that should look similar to the screenshot below.
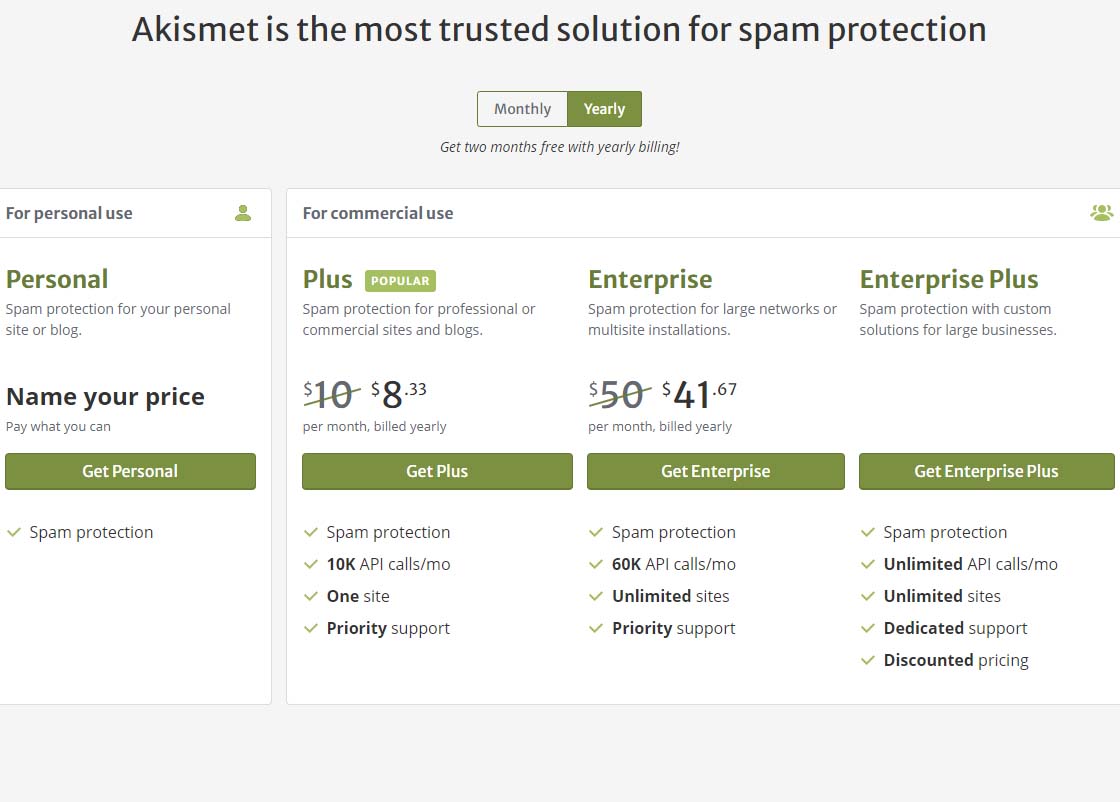 Akismet offering pricing page
Akismet offering pricing pageTo get the free version of Akismet comment spam protection, you will need to click on the Get Personal button on the above page.
Once you’ve done that, you should see a page similar to the one below. Before attempting to fill out anything on this page, we need to set that $36 / YEAR to $0 / YEAR. Click on the $36 / YEAR box and drag it to the left.
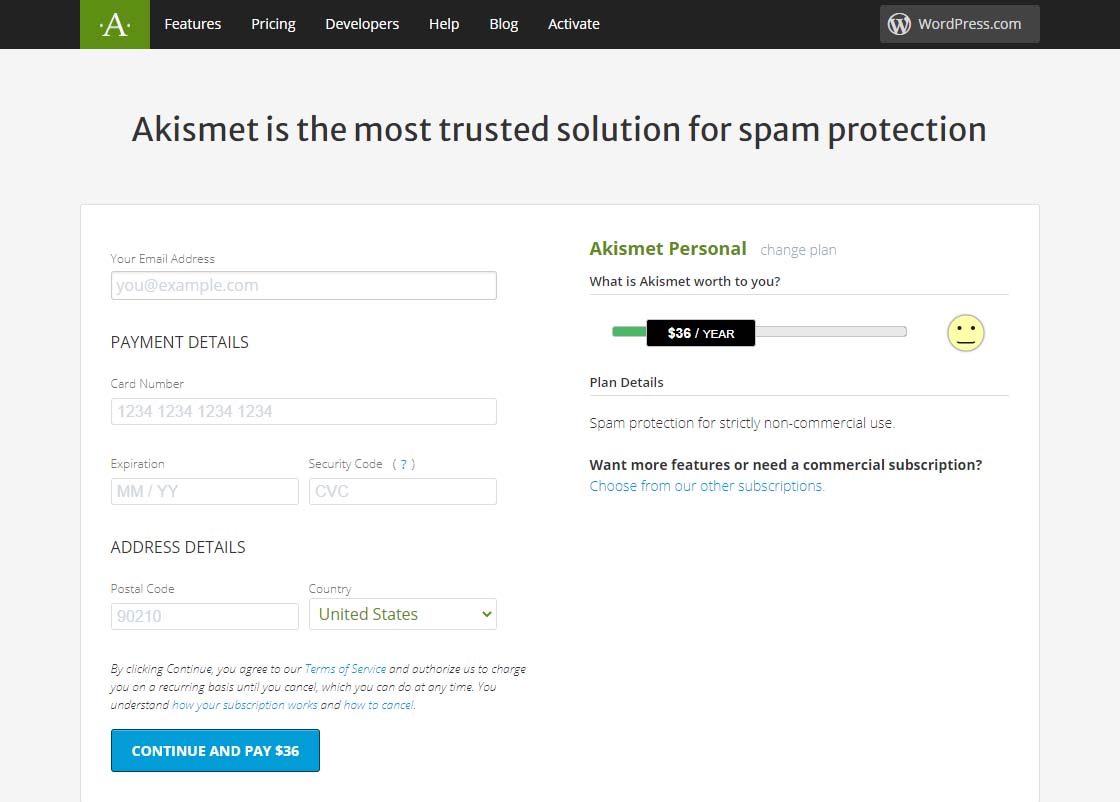 Akismet Default $36 per year page
Akismet Default $36 per year pageDragging that $36 / YEAR box to the left should change the page to display something like the one below showing 0$ / YEAR. You can also see that the information to fill in has changed.
Akismet $0 per year page
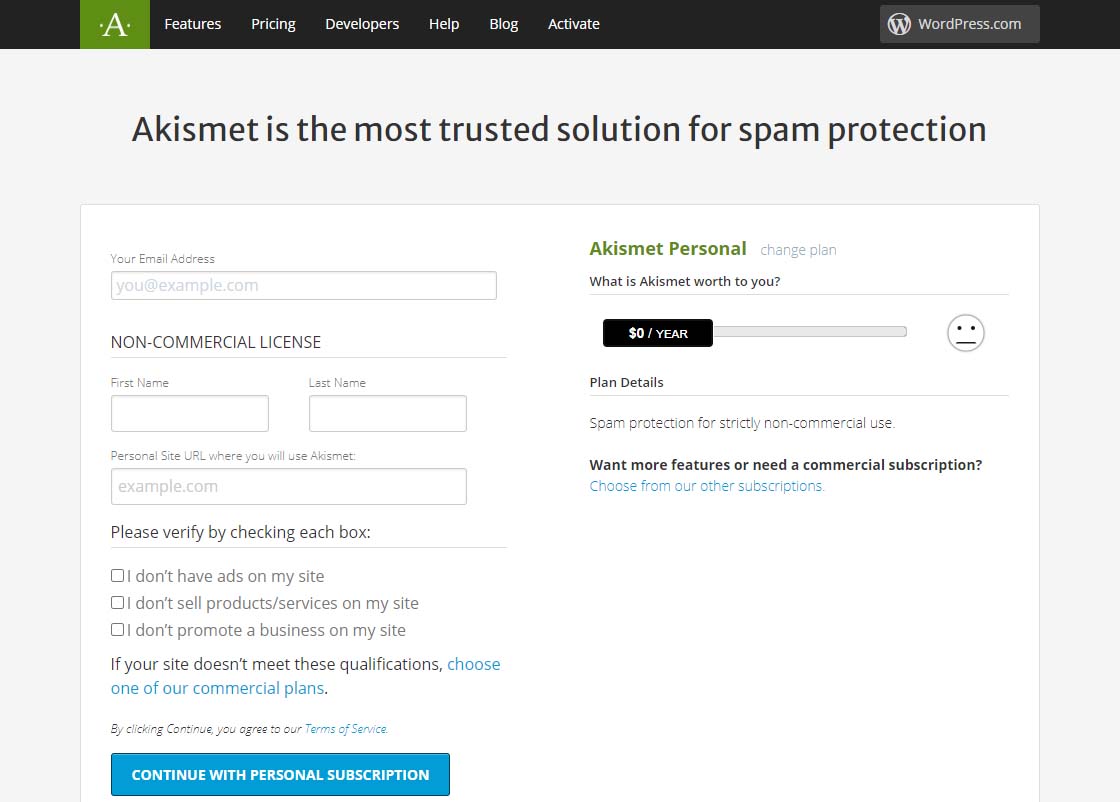 Akismet $0 per year page
Akismet $0 per year pageNow fill in the information completely. Note that you need to be able to check all three checkboxes indicating the following:
-
-
- you don’t have ads on your site
- you don’t sell products/services on your site
- you don’t promote a business on your site
If these are the case, then you will qualify for a free, personal plan.
All you have to do once you have gotten this far is follow the directions on the page below.
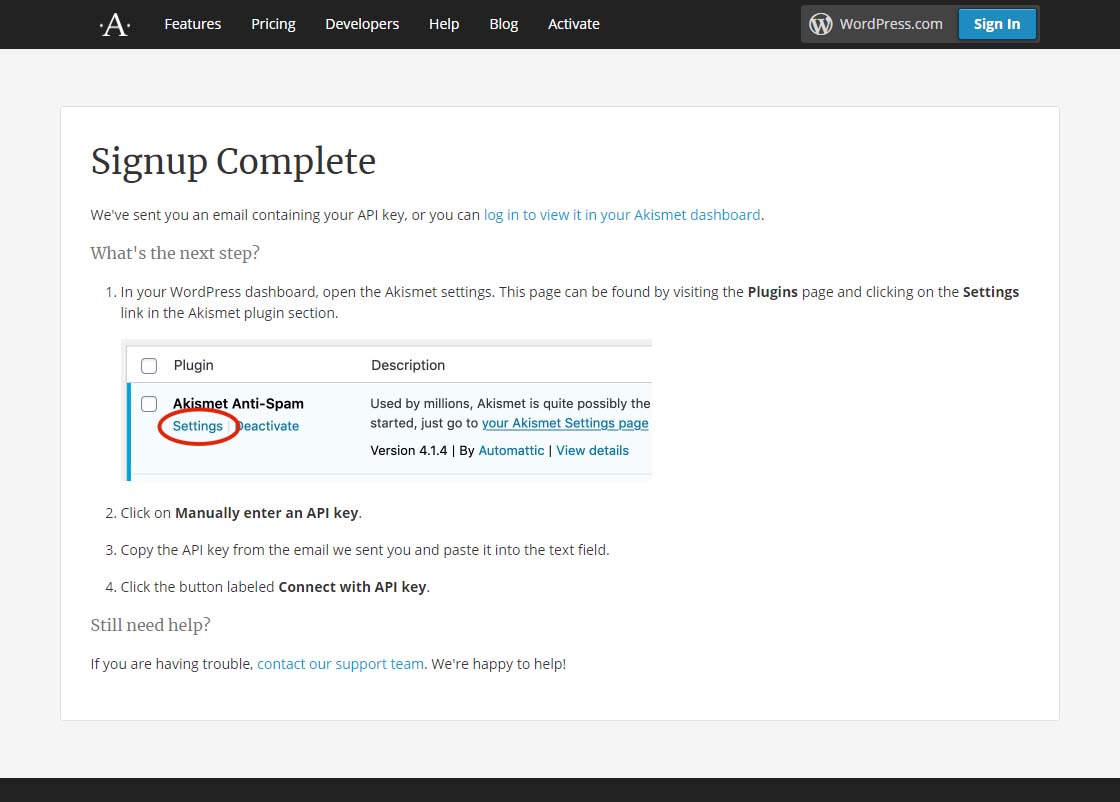 Akismet signup complete page
Akismet signup complete pageFinally, it is suggested that while on that settings page in Akismet, you can choose to show the number of approved comments beside each comment author and choose whether to show a privacy notice or not. Then just click the Save Changes button and you are on your way!










by Charles Oropallo | Nov 15, 2020 | Do-It-Yourself, Technical Help, WordPress
Every piece of popular software gets updated over time. PHP is no different.
PHP 7.4 is the latest version of PHP 7 at the time of this writing. It was originally rolled out November 28, 2019 and will receive security support until November 28, 2022. It also appears that PHP 7.4 may be the last of the PHP 7 releases, as PHP 8.0 was rolled out on November 26, 2020.
This is all great news, since each newer PHP version so far has continued to provide:
- considerable (but not total) backward compatibility
- faster execution speeds
- greater security.
We’ve seen many PHP upgrades since running WordPress over many, many years. Our preliminary testing has always shown that many WordPress plugins and themes don’t work seamlessly with new versions of PHP as they are rolled out. As for PHP 7.4, the WordPress core and its latest default themes do. Unfortunately, many sites will simply break if caution isn’t taken to ensure all of their components – the core, the plugins and the themes – are PHP 7.4 compliant. For this reason, we usually don’t switch PHP to the later version until we are confident most things will work. When you think about the many thousands of themes and plugins out there for WordPress, it is no surprise that sometimes this takes longer than a year.
WordPress PHP notifications
PHP versions older than PHP 7.2 now trigger the red circle with an exclamation point PHP notification that administrative users see in the WordPress dashboard.
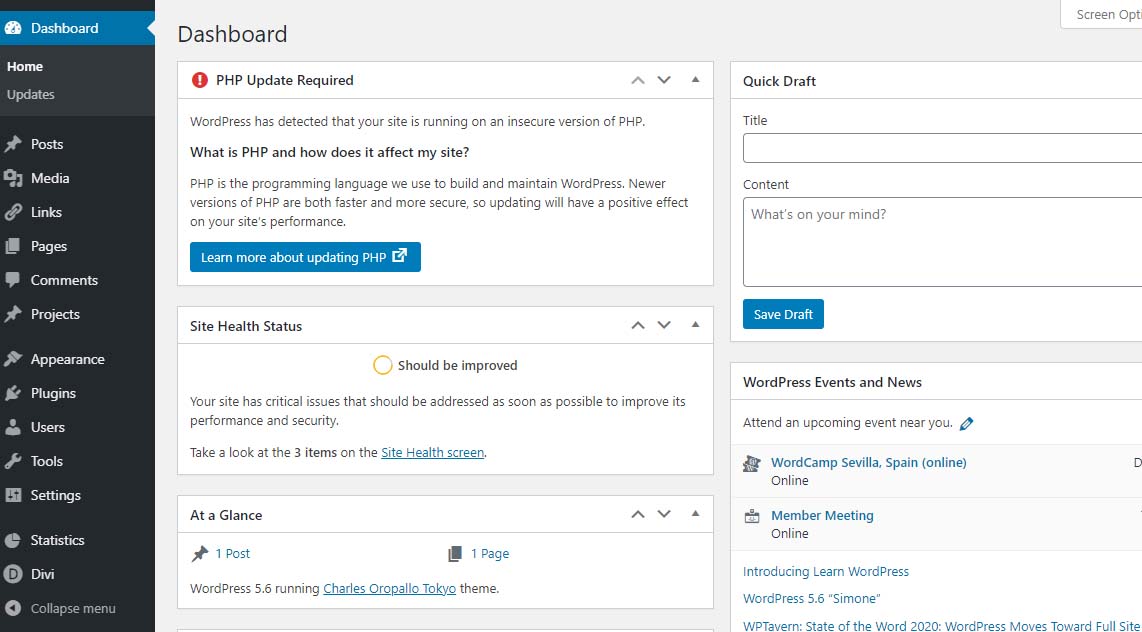 PHP update required notification
PHP update required notification
Site Health Status – Should be improvedBear in mind that WordPress only issues a warning about 7.1 and lower. The red notice in the dashboard is not shown for higher versions. Navigating to Tools > Site Health yields more details about site health.
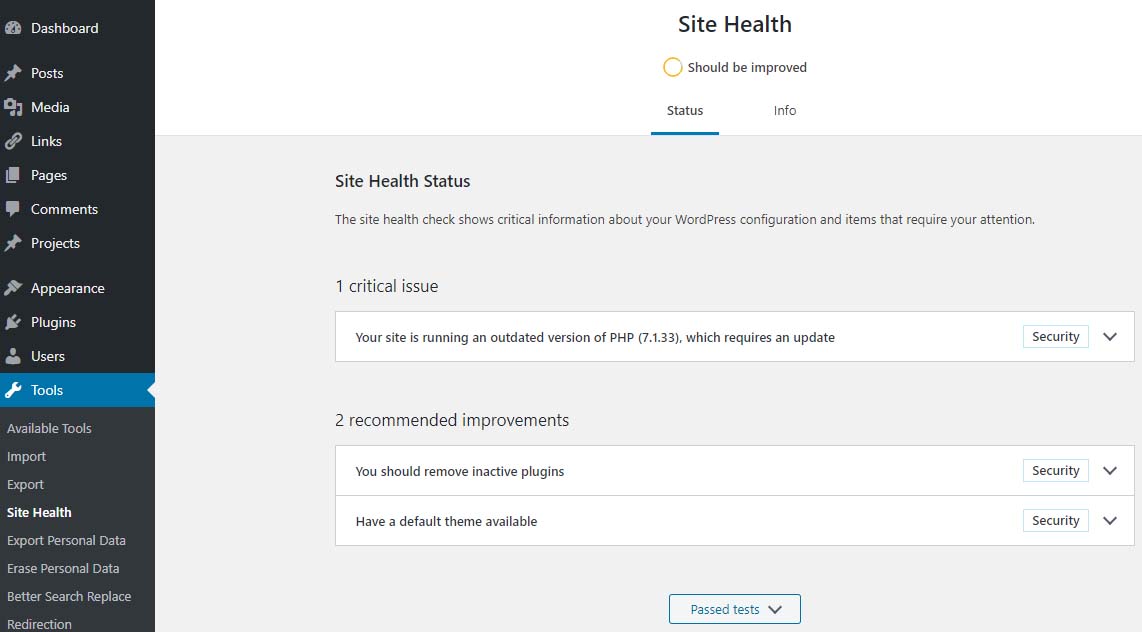 Site Health – Should be Improved
Site Health – Should be Improved
Site Health Status – 1 critical issue – running outdated version of PHP 7.1 requires an updatePHP 7.2 just went to end of life November 30, 2020 – hence the red PHP update required notice that shows in the dashboard for anything older than 7.2 doesn’t show if you are running PHP 7.2 and above.
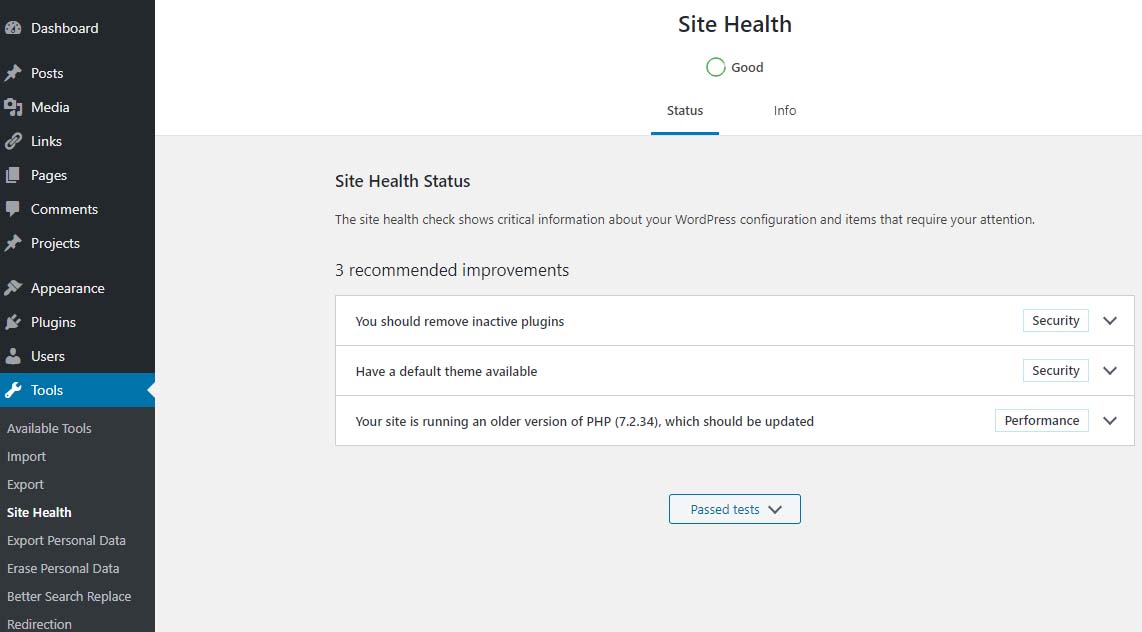 Site Health Status – Good
Site Health Status – Good
PHP 7.2 which should be updatedIf you are running PHP 7.3 (or newer) you will not get the red notice described above. However, in the site health you will see an indication stating “Your site is running an older version of PHP (7.3.x) which worries many when they see it.
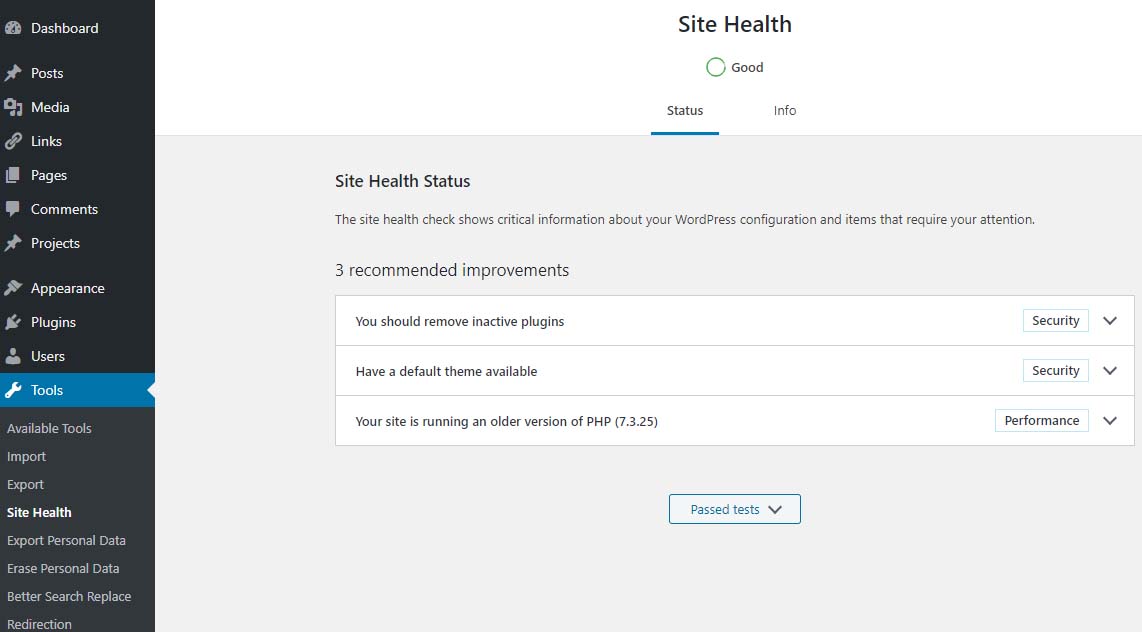 Site Health – Good
Site Health – Good
Site Health Status – 1 recommended improvement – running an older version of PHP – PHP 7.3.25The fact is that PHP 7.3 will be receiving security updates until December 6, 2021. Given that, there is plenty of time to get ready for PHP 7.4.
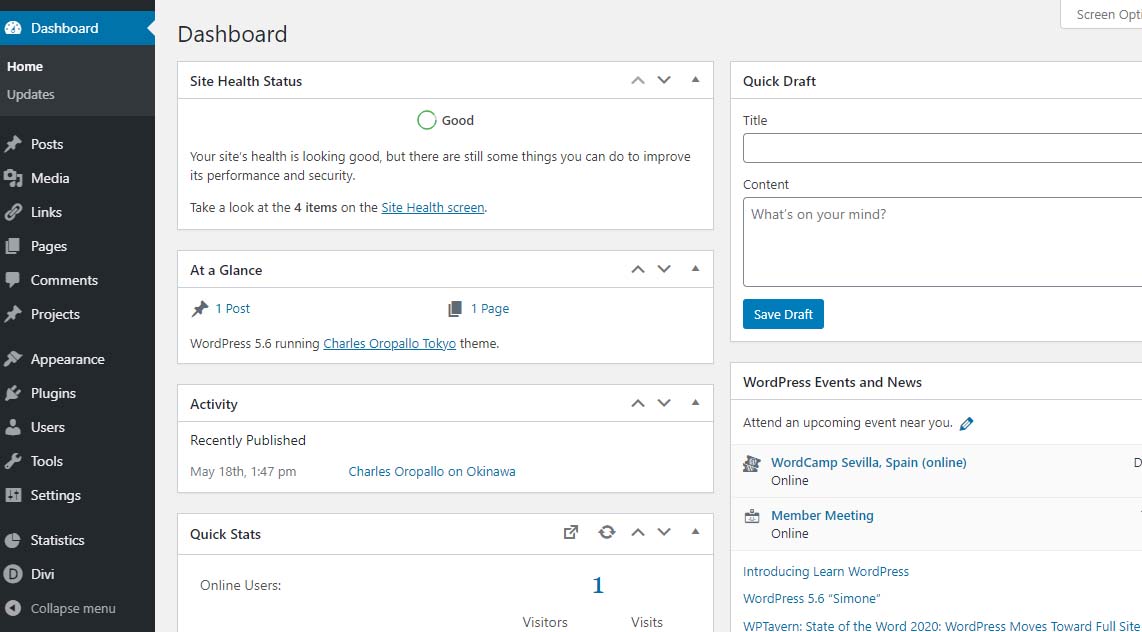 Site Health Status – Good
Site Health Status – Good
PHP 7.2 and aboveThe plan at CharlesWorks is to make PHP 7.4 available in the upcoming months. When that happens, you will notice that each of the PHP 7.x versions you see in the DirectAdmin interface will be bumped up by one version. So you will always still be able to go back to 7.3 if needed.
PHP 8.0 was released on November 26, 2020 with an expected security support date of October 26, 2023. There appears to be more incompatibility between it and PHP 7. CharlesWorks would not expect to roll this version out until nearer the end of 2021. Let’s give the world a chance to find all of the bugs for us.










by Charles Oropallo | Nov 12, 2020 | Do-It-Yourself, Technical Help, The CW Corner, Website Development, Website Updates, WordPress
Sometimes in a WordPress website an issue develops where when loading images into media library, only a blank thumbnail shows. It appears a space is created in the database for the picture but there is no content in it.
After testing compatibility of plugins, themes, php, etc., the problem persisted.
To resolve this, one can navigate here logged into WordPress as an administrator:
Go to Dashboard > Settings > Media
Make sure the correct default file path is showing there. When troubleshooting this issue on a site that was unable to upload media files, the file path was shown as:
/home/username/domains/thedomainname.com/private_html/wp-content/uploads
Note that the “username” and “thedomainname.com” in the above and below path examples will be the Linux username and the actual site domain name respectively that you are troubleshooting.
The fix
When this path was removed, the image file upload worked normally again and the problem appeared to be solved.
Possible Reasoning or Causes
In the DirectAdmin path structure, there are two places the website’s servable coding (like WordPress or HTML sites or Joomla, etc.) might be stored:
/home/username/domains/thedomainname.com/public_html
or
/home/username/domains/thedomainname.com/private_html
The “public_html” folder is where DirectAdmin normally places the website’s code (again, referring to all the files and programs that make up the actual WordPress or HTML or Joomla site’s coding, etc.).
The “private_html” folder is where DirectAdmin normally tries to place the website’s code when its content is encrypted. That’s why there is an option in DirectAdmin’s site control panel that allows one to “Use a symbolic link from private_html to public_html”. This option allows for using the same data in http and https.
The suspicion here is that a setting got changed or an update occurred causing the WordPress system to use the private_html setting when the site resides in public_html. Removing the file path from the settings forced WordPress to use where the system actually defaulted to – which cleared the problem.
We may never know how the setting actually got bunged up, but it is an easy fix once it is.










by Charles Oropallo | Oct 16, 2020 | Internet, SEO
Almost all businesses get the usual spam SEO (Search Engine Optimization) phone calls.
Recently, one of my web clients took one. As a result of such calls, she emailed me. She expressed a lot of concern about having been told very negative things about her web traffic and website operation. It sounded like he was trying to get her to spend money. Money she’d never see a return on her investment for.
High-pressure sales tactics are something I have instructed staff in all our years in business to avoid. CharlesWorks policy forbids selling clients anything they don’t need. The difficulty is that there are so many spammers and scammers out there sending the same messages that people believe them. You can tell the same lie a thousand times and it’s still a lie.
Among the thousands of websites we’ve handled, her particular business is very unique – especially during the COVID-19 epidemic. Her classes are limited regarding how many people she can have in them at any given time. I told her that she is the one who knows best what should be on her website. And she is the one who knows best what she has to offer and when she can offer it.
The nature of her business, it seemed to me, is based more on a following she has developed over time. And she is limited as to how many people at a time she can physically handle. And – much as I hate to say this – COVID is going to remain a thought in many people’s minds – at least through this upcoming winter season. Things will change when a vaccine is widely available. However, common sense dictates it will be a while before everyone generally has access to it.
I suggested she shouldn’t spend more than she absolutely has to – to just keep her business operational. Those small business owners who can stay in business through this pandemic will be the ones who do great once they reach the other side of this.
It’s troubling that someone had pressured her enough to do work on her site that she became stressed over it. Sales people who proceed with such a hard sell attitude are clearly desperate for work. Desperate people are not working with their customer’s best interest in mind. My advise is to not talk to these people.
My suggestions for dealing with these really hard line sales calls are:
- “Remove me from your calling list.” Tell them to remove you from their calling list. Once you say those words, they are supposed to do so by law. I regularly tell spammers this, and they generally don’t bother to call back.
- Block their phone number. Block their number through whatever mechanism your telephone carrier has set up to do that. I do this on a pretty regular basis with the robocalls (which are actually illegal in most cases) and take a few minutes to report them at the https://www.donotcall.gov/report.html site.
- Visit the National Do Not Call Registry. Go to https://www.donotcall.gov where you can put your phone numbers on the National Do Not Call Registry. Mine have been on this for many years.
While these suggestions don’t stop all the spam calls you’ll get, they do stop many.
Every small business owner can and should review their website. They should ensure that everything is up to date for offerings and schedules. That only costs them a few minutes. Because CharlesWorks charges for changes by the minute, those kinds of changes only incur those minutes of charges.
I hope this is helpful to you!










by Charles Oropallo | Sep 2, 2020 | Domains, Internet, SEO, The CW Corner
We’ve published plenty of information in the past about domain names. We’re always learning a little more and how to explain information to out clients as time passes.
Whether your domain name is for personal use or for your business, we hope you find the following tips to be helpful.
Keywords
Having words pertinent to your business in your domain are increasingly important. Simplistically put, search engine algorithms (the math formulae used to compute the importance or value of words contained in your site) rank the importance of web sites according to words. Many businesses use a domain name to describe the name of their business and, in addition to that, own domains which contain keywords which are present in their website.
Association
If possible, you should use the name of your business as all or part of one of your domain names. This will make it easier for your clients or potential clients to remember you and to find you on the web (like CharlesWorks.com – CharlesWorks is the name of our business).
General Names
More general domain names are most likely already registered to other businesses (of course it doesn’t hurt to check with us first). It’s still a good idea to have more general name(s) associated with your business as one of your domains (that’s why we also own HostingNH.net, which will take visitors to our CharlesWorks.net site).
TLDs
TLDs stands for Top Level Domains. TLDs are the extensions on the tail end of the domain, such as .biz, .club, .co, .com, .net, .org, .ws, etc. The most popular TLDs are .com and .net. If you find that your domain is already registered, you might try for an alternate TLD (for example, RobinSnow.com was already taken, so Robin acquired and uses RobinSnow.net).
Hyphenated Names
Although you can obtain them, we recommend not using hyphens for your business domain name. Most people who are searching for your site will not use a hyphen. You are better off to try a different TLD or a variation of your domain name.
Variations
Variations can be an option if your general business name is already registered (for example ScrapbookCabin.com was not available to one of our clients, so at the time she registered NHScrapbookCabin.com instead).
Relinquishing or giving up existing names
We have seen many horror stories concerning giving up existing domain names. Sometimes one will end up having to get a similar domain name because control over the preferred name could not be gained. An example would be where another party has control over one’s .com name and the website is down and the webmaster cannot be reached or is non-responsive. If we are to take over the services we would recommend getting the .net to the original .com of the domain name if it were available. This allows us to get the site up and at least people can be sent to that site pending transfer of the .com when it is possible. In some cases it never became possible and the site will continue using the .net domain.
Once a domain name has been in service, traffic is generated to it. For that reason, many expired or relinquished domain names are snatched up. One situation like this in the Manchester NH area involved a church giving up a domain name they did not want to use anymore (it was a version of the Church’s name that had been in use for many years and they just decided to change it and dropped the domain name). It saved them about $15 a year. However, the embarrassment was priceless when a porn company acquired that domain name and put a porn site up on it. The annual cost of a domain is truly cheap insurance against one’s domain name being used for phishing, porn, Viagra, or whatever.
There is absolutely no obligation of any kind to click the red button below and check out your domain possibilities!

Already have a domain name? Click on the red button below to transfer it so we can get you online here at CharlesWorks!

Or CALL CharlesWorks at 603-924-9867 9 am – 5 pm Monday through Friday or go to https://CharlesWorks.com/contact outside of regular hours and we will help you find one!










by Charles Oropallo | Aug 5, 2020 | Do-It-Yourself, Internet, Monadnock Shopper News, Shopper News, Website Development, Website Updates, WordPress
Something many folks overlook is occasionally checking their website’s functionality. I recommend doing this every couple weeks, but at minimum once a month.
Most websites and the servers they are on are subjected to ongoing software updates. Unless you are paying an additional fee for maintenance checks, it’s normal for things to occasionally break due to updates.
Most website owners are not paying additional fees for such maintenance. This means you really need to take the time to check:
– that the site appears to work properly
– that your hours of operation are correct
– that any website forms are working
– that email addresses are correct
The site operation and forms are most susceptible to software updates. If you have a good web developer, the fixes will happen quickly and it will not cost you too much.
Website maintenance should be thought of like automotive maintenance. We get oil changes. We get inspections. We even make modifications and do repairs to keep our vehicle operating the way we want. And our older vehicles can cost more to upkeep – just like older websites. As websites age, more work needs to be done to keep them secure and working as originally intended.
So check your site every now and then to keep things working and have the correct information out there!










by Charles Oropallo | Jul 22, 2020 | Internet, Monadnock Shopper News, Shopper News, The CW Corner
 Masks help keep us all safe from the novel coronavirus
Masks help keep us all safe from the novel coronavirusAround mid-march of 2020 the pandemic started getting taken seriously here in New Hampshire. Quickly workforces transitioned to working remotely wherever possible. Now we’re four months into it. We’d hoped the pandemic would be relaxing a bit but it appears to just be getting ramped up these days in much of the rest of the country.
Most have discovered that working remotely is not as simple and easy as it seemed at first. Now we can see some of the true difficulties.
Here is the one major tip I’ll offer today: work remotely like the boss is watching. Remember that the boss probably IS watching. When you are at that remote workstation behave as though you’re at your office workspace. Seriously. Would you go to work without washing or taking care of your personal appearance? Why risk having an unscheduled remote meeting with fellow employees totally unprepared? Poor impressions will certainly not help you when it comes to reviews.
There’s no reason to not really shine at your job remotely. Think about how fortunate you may be at not having to commute to work. And the ability to make meetings allows you to lose far less time previously afforded to travel.
The key to making remote working feasible is tied to communication. You must communicate either via text, phone, email or Zoom type meetings often enough to stay connected to your work force to complete tasks.














































 European Union General Data Protection Regulation Compliant
European Union General Data Protection Regulation Compliant